Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "password security"
-
An incident which made a Security Researcher cry
--------------------------------------------------------
I was working on my laptop finishing up my code while waiting for the flight which was late . Meanwhile two guys (I'm gonna call them Fellas) in black suit and shades came to me
Fella : Sir you have to come with us .
Me : *goes along with them*
Fella : Sir please proceed *points towards the door . The room has a round table with some guys discussing something *
Fella 1 : Your passport please
Me : *Hands over the passport*
Fella 1 : Where are you traveling to sir?
Me : India
Fella 1 : Put your laptop in the desk sir.
Me : Sure thing
Fella 2 : What were you doing there? *Taps the power button*
Me : Just finishing up my work .
Fella 1 : Or hacking our systems?
Me : Seriously?
Fella 2 : The password please .
Me : Here you go
*5 minutes have passed and he still can't figure out how to use the machine*
Fella 2 : Which Windows is this?
Me : It's Linux
Fella 1 : So you are a hacker .
Me : Nope
Fella 1 : You are using Linux
Me : Does it matters?
Fella 1 : Where do you work?
Me : *I won't mention here but I told him*
Fella 2 : So what do you do there?
Me : I'm a Security Researcher
Fella 1 : What's your work?
Me : I find security holes in their systems .
Fella 1 : That means you are a hacker .
Me : Not at all .
Fella 2 : But they do the same and they use Linux .
Me : You can call me one .
*After 15 minutes of doo-laa-baa-dee-doo-ra-ba-doo amongst them I dunno what they were talking , they shutdown the computer and handed over it to me*
Fella 2 - So you are somewhat like a hacker .
Me - *A bit frustrated* Yes.
##And now the glorious question appeared like an angel from river ##
Can you hack Facebook?
Me - 😭😭😭28 -
Me: how's your password security?
Them: of course we value security very highly, our passwords are all hashed before being stored.
Me: what hashing algorithm?
Them: oh we hash it with sha and then place that in a table indexed by the password.
Indexed. By. The fucking. Password.16 -
Creating a new account is always fun...
"This Is My Secure Password" <-- Sorry, no spaces allowed.
"ThisIsMySecurePassword" <-- Sorry, Passwords must include a number
"ThisIsMySecurePassword1" <-- Sorry, Passwords must include a special character
"ThisIsMySecurePassword 1" <-- Sorry, no spaces allowed
"ThisIsMySecurePassword%1" <-- Sorry, the % character is not allowed
"ThisIsMySecurePassword_1" <-- Sorry, passwords must be shorter than 16 characters
"Fuck" <-- Sorry, passwords must longer than 6 characters
"Fuck_it" <-- Sorry, passwords can't contain bad language
"Password_1" <-- Accepted.25 -
Tldr :
Office Building : 1
Population: 5000
Number of PC users: 5000
No of Spare mice: 0
Day 1:
Training period commences.
My mouse laser sensor doesn't work.
Solution: Use this mouse to log in to your system.
Open the company portal.
Connect to vpn.
Enter username password.
Create a ticket for mouse replacement.
Done.
Day 3
I bring my own mouse.
Confiscated at security.
Becomes a security violation.
Day 9
I get a call from helpdesk.
Agent- what is the problem?
Me- my mouse is not working.
Agent- why?
Me- what do you mean? Something is wrong with the sensor.
Agent- clean the sensor.
Disconnects call.
Marks ticket as resolved.
Me- WTF just happened!
Naturally, I escalate the issue.
Day 15
Level 2 Agent- what happened? Why have you escalated the issue?
Me- I need a mouse, waiting since 2 weeks.
Him- No mouse is available
Me- you don't have a single spare mouse available in an office with 5000 PC users?
Him- no they're out of stock.
Me- when will it be back in stock?
Him- we will 'soon' launch a tender for quotations from sellers.
Me- time?
Him- 1 week.
Day 34
I email the head of supplies for the city office. Next day I get a used super small mouse, which doesn't have a left button. Anyways, I've given up hope now.
Day 45
I become a master at keyboard shortcuts.
Finish my training.
Get transferred to another city.
No mouse till date.
Surprisingly, this was one of the top recruiters in my country. Never knew, MNCs can be so so inefficient for such simple tasks.
Start-ups are way better in this regard. Latest tech, small community, minimal bureaucracy and a lot of respect and things to learn.15 -
Had three servers running in prod. For extra security all of them were encrypted (hdd encryption) just in case.
"mate, servers need a quick reboot, that alright?"
Me: yeah sure!
"oh hey they're encrypted, what's the password?"
Uhm.....
😐
😓
😨
😵😨😮😧😫
😲😶😭
Yeah, i also forgot to turn on the backup process...17 -
Got my new workstation.
Isn't it a beauty?
Rocking a Pentium II 366 MHz processor.
6 GB HDD.
64 MB SDRAM.
1 minute of battery life.
Resolution up to SXGA (1280x1024)
Removable CD-Rom drive.
1 USB port (we like to use dongles, right?)
Also it has state of the art security:
- No webcam
- No Mic
- Removable WiFi
- I forgot the password
And best of all:
It as a nipple to play with!! 31
31 -
What the actual fuck? Person (or people!) who devised this password policy, you are an idiot (or idiots - all of you). You are stupid and insane and have no idea about security or user experience.
 14
14 -
So our public transportation company started to sell tickets online with their brand new fancy system.
• You can buy tickets and passes for the price you want
• Passwords are in plaintext
• Communication is through HTTP
• Login state are checked before the password match so you can basically view who is online
• Email password reminders security code can be read from servers response
Oh and I almost forgot admin credentials are FUCKING admin/admin
Who in the fucking name of all gods can commit such idiocracy with a system that would be used by almost millions of people. I hope you will burn in programming hell. Or even worse...
I'm glad I'm having a car and don't have to use that security black hole.15 -
Me: *enters password on phone (long PIN)*
Person next to me is looking at my phone WHILE I enter my password, and as I look at him, he doesn't even turn away and even has the nerve to say:
"Wow, why do you have such a long password!"
Μy answer: "Because of security reasons."
What I actually wanted to say:
"Because of pieces of SHIT like you who can't keep their eyes to themselves, even when PASSWORDS are involved, you FUCK! Guess why everytime I enter a password in public, I have to dim my screen and turn my screen sideways? Because of fuckheads like you, not knowing shit about privacy and security! Fuck you!"7 -
!rant
So it turns out that my dad accidentally took my spare laptop on a work trip. He's about as non-tech as you can get, and that laptop runs...Arch Linux. Yeah.
(call from dad)
M: hi dad
D: what's your desktop password?
M: (confused) {Password}
D: okay.
(cuts the call)
M: *shrug*
(call from dad)
M: hi dad
D: so where is PowerPoint?! where's the Windows button?! I've been at this for half an hour now and I have to edit a presentation for tomorrow!!
M: (realizes what's happened) oh...uh...dad...that's.. Linux...
D: don't you people do anything the way it's supposed to be done?
M: uh...
D: ugh! So you can't edit PPTs on this?
M: (processing...LibreOffice isn't installed on the laptop, and he will have to use the command line to connect to the internet to use Office Online or Google Slides since the Deepin WiFi module keeps fucking up for some reason)
D: well?
M: (internal sigh) No, you can't edit PPTs on that.
D: wow.
(cuts the call)
He either thinks we're all useless or that we have godlike computer skills to be able to edit PPTs on Linux. Oh well.
(He managed to use the hotel's "workstation" to get it done, so all is well. I should tell him to change his password though, hotel computers have rubbish security.)13 -
1. Create user on website.
2. Receives mail with username and password.
3. Changes password.
4. Receives mail with new password.
5. Delete account and look for another service.3 -
Trying to login...
"Sorry your password is expired. You have to change the password every 60 days".
«Oooh, c'mon...» Inserting a new password...
"The password must contain at least 1 lowercase letter, 1 uppercase letter, 2 numbers and 1 non-alphanumeric character.
«Please, fuck off and die...» Typing again and eventually entering to private area...
My phone vibrate, there is a new SMS: "Your new password is H0lySh1t!"
WTF. Are you serious?10 -
PM: We need security on signup, the password entry should contain "A capital letter, 2 numbers, a symbol, an inspiring message, a spell, a gang sign, a hieroglyph and the blood of a virgin."
ME: 8
8 -
Even though I'm a web developer I work in a very small IT department, which includes just me and my colleague.
Yesterday we got a pretty usual request. Someone forgot the password to an excel file. We already started a brute force attack, but we had some fun going through the worst passwords we ever stubbled over in our carrier.
He was like:"Maybe it's just his name?"
Me: "Oooh or maybe it's just the brand and 123?"
We laughed a lot. Not really considering we could crack this "important" file.
But it really worked out. The password was the brand of the business unit and "2017".
I've sent everthing back to the user, telling him exactly how we cracked it... His answer was:"Oh yeah! I knew it was something easy, so me and x could remember it easily!"
...
Why do you forgive easy passwords anyway? If I can crack it within 5 minutes... Everyone can! ...
And if you do it to "remember it easily"? Why the fuck don't you remember it?4 -
Hello!
I'm a member of an international hacker group.
As you could probably have guessed, your account [cozyplanes@tuta.io] was hacked, because I sent message you from it.
Now I have access to you accounts!
For example, your password for [cozyplanes@tuta.io] is [RANDOM_ALPHABET_HERE]
Within a period from July 7, 2018 to September 23, 2018, you were infected by the virus we've created, through an adult website you've visited.
So far, we have access to your messages, social media accounts, and messengers.
Moreover, we've gotten full damps of these data.
We are aware of your little and big secrets...yeah, you do have them. We saw and recorded your doings on porn websites. Your tastes are so weird, you know..
But the key thing is that sometimes we recorded you with your webcam, syncing the recordings with what you watched!
I think you are not interested show this video to your friends, relatives, and your intimate one...
Transfer $700 to our Bitcoin wallet: 13DAd45ARMJW6th1cBuY1FwB9beVSzW77R
If you don't know about Bitcoin please input in Google "buy BTC". It's really easy.
I guarantee that after that, we'll erase all your "data" :)
A timer will start once you read this message. You have 48 hours to pay the above-mentioned amount.
Your data will be erased once the money are transferred.
If they are not, all your messages and videos recorded will be automatically sent to all your contacts found on your devices at the moment of infection.
You should always think about your security.
We hope this case will teach you to keep secrets.
Take care of yourself.
>> RE >>
Well f### you, thanks for telling my password which is obviously fake. I have sent your details to the local police department, shall rest in peace. Don't earn money by this kind of action. STUPID!17 -
haveibeenpwned: MASSIVE SECURITY BREACH AT COMPANY X, MILLIONS OF RECORDS EXPOSED AND SOLD, YOUR DATA IS AT RISK, please change your password!
Company X website: Hey your password expired! Please change it. Everything's fine, wanna buy premium? The sun is shining. Great day.1 -
*enters password*
*misspells a letter*
*OMG BACKSPACE! BACKSPACE!*
*retypes whole password again* 😂😂6 -
Great news, our company's has a brand new security-first product, with an easy to use API and a beautiful web interface.
It is SQL-injection-enabled, XSS-compatible, logins are optional (if you do not provide a password, you are logged in as admin).
The json-api has custom-date formats, bools are any of "1", "0", 1, 0, false or null (but never true). Numbers are strings or numbers. Utf-8 is not supported. Most of our customers use special characters.
The web interface is using plain bootstrap, and because of XSS it is really easy to customize everything.
How the hell this product got launched is beyond me.10 -
I recently found a company that used employee social security numbers as their login username and their MMDDYYYY as their password (which could not be changed) also their entire network was using a router with no wifi password set. :/8
-
*signs up for Skillshare*
> Sorry, your password is longer than our database's glory hole can handle.
> Please shorten your password cumload to only 64 characters at most, otherwise our database will be unhappy.
Motherf-...
Well, I've got a separate email address from my domain and a unique password for them. So shortening it and risking getting that account stolen by plaintext shit won't really matter, especially since I'm not adding payment details or anything.
*continues through the sign-up process for premium courses, with "no attachments, cancel anytime"*
> You need to provide a credit card to continue with our "free" premium trial.
Yeah fuck you too. I don't even have a credit card. It's quite uncommon in Europe, you know? We don't have magstripe shit that can go below 0 on ya.. well the former we still do but only for compatibility reasons. We mainly use chip technology (which leverages asymmetric cryptography, awesome!) that usually can't go much below 0 here nowadays. Debit cards, not credit cards.
Well, guess it's time to delete that account as well. So much for acquiring fucking knowledge from "experts". Guess I'll have to stick to reading wikis and doing my ducking-fu to select reliable sources, test them and acquire skills of my own. That's how I've done it for years, and that's how it's been working pretty fucking well for me. Unlike this deceptive security clusterfuck!14 -
First rant, please take pity on the noob! 😐
Recently I've secured many of my user accounts spread throughout the internet. Using the same old password for everything is bad for security and for mental health! 😫
Since I was on the mood, I've tried to do a 'break glass' scenario, simulating an attacker that possessed my Gmail account credentials. "How bad can it be?" I've thought to myself...
... Bad. Very bad. Turns out not only I use lots of oauth based services, I also wasn't able to authenticate back to Google without my pass.
So when you get home today, try simulating what would happen if someone got to your Google or Facebook account.
Makes you consider the amount of control these big companies have over your life 😶15 -
So according to some reddit user IKEA sends your password as a GET parameter in plain text.
https://reddit.com/r/CrappyDesign/...
Seems to be a network authentication thingy, but still 🤔 34
34 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
I'm trying to sign up for insurance benefits at work.
Step 1: Trying to find the website link -- it's non-existent. I don't know where I found it, but I saved it in keepassxc so I wouldn't have to search again. Time wasted: 30 minutes.
Step 2: Trying to log in. Ostensibly, this uses my work account. It does not. Time wasted: 10 minutes.
Step 3: Creating an account. Username and Password requirements are stupid, and the page doesn't show all of them. The username must be /[A-Za-z0-9]{8,60}/. The maximum password length is VARCHAR(20), and must include upper/lower case, number, special symbol, etc. and cannot include "password", repeated charcters, your username, etc. There is also a (required!) hint with /[A-Za-z0-9 ]{8,60}/ validation. Want to type a sentence? better not use any punctuation!
I find it hilarious that both my username and password hint can be three times longer than my actual password -- and can contain the password. Such brilliant security.
My typical username is less than 8 characters. All of my typical password formats are >25 characters. Trying to figure out memorable credentials and figuring out the hidden complexity/validation requirements for all of these and the hint... Time wasted: 30 minutes.
Step 4: Post-login. The website, post-login, does not work in firefox. I assumed it was one of my many ad/tracker/header/etc. blockers, and systematically disabled every one of them. After enabling ad and tracker networks, more and more of the site loaded, but it always failed. After disabling bloody everything, the site still refused to work. Why? It was fetching deeply-nested markup, plus styling and javascript, encoded in xml, via api. And that xml wasn't valid xml (missing root element). The failure wasn't due to blocking a vitally-important ad or tracker (as apparently they're all vital and the site chain-loads them off one another before loading content), it's due to shoddy development and lack of testing. Matches the rest of the site perfectly. Anyway, I eventually managed to get the site to load in Safari, of all browsers, on a different computer. Time wasted: 40 minutes.
Step 5: Contact info. After getting the site to work, I clicked the [Enroll] button. "Please allow about 10 minutes to enroll," it says. I'm up to an hour and 50 minutes by now. The first thing it asks for is contact info, such as email, phone, address, etc. It gives me a warning next to phone, saying I'm not set up for notifications yet. I think that's great. I select "change" next to the email, and try to give it my work email. There are two "preferred" radio buttons, one next to "Work email," one next to "Personal email" -- but there is only one textbox. Fine, I select the "Work" preferred button, sign up for a faux-personal tutanota email for work, and type it in. The site complains that I selected "Work" but only entered a personal email. Seriously serious. Out of curiosity, I select the "change" next to the phone number, and see that it gives me four options (home, work, cell, personal?), but only one set of inputs -- next to personal. Yep. That's amazing. Time spent: 10 minutes.
Step 6: Ranting. I started going through the benefits, realized it would take an hour+ to add dependents, research the various options, pick which benefits I want, etc. I'm already up to two hours by now, so instead I decided to stop and rant about how ridiculous this entire thing is. While typing this up, the site (unsurprisingly) automatically logged me out. Fine, I'll just log in again... and get an error saying my credentials are invalid. Okay... I very carefully type them in again. error: invalid credentials. sajfkasdjf.
Step 7 is going to be: Try to figure out how to log in again. Ugh.
"Please allow about 10 minutes" it said. Where's that facepalm emoji?
But like, seriously. How does someone even build a website THIS bad?rant pages seriously load in 10+ seconds slower than wordpress too do i want insurance this badly? 10 trackers 4 ad networks elbonian devs website probably cost $1million or more too root gets insurance stop reading my tags and read the rant more bugs than you can shake a stick at the 54 steps to insanity more bugs than master of orion 312 -
- I'm forced to do dev on Windows with no admin because security
- We receive patches to critical systems from outside company on FTP secured with password "asd123" and install them without reading because fuck security2 -
I now know another person's password without even wanting to.
He was sitting in the row in front of me, logging into our course page and then *brrrrraaaaapppp* - ran his index finger along the top number row and hit enter.
1234567890
I don't even know what to say.12 -
Not exactly a security bug, but there was a company that made a Django app for some internal work and later open sourced it. I was browsing through the code and I saw that the config file had an IP address and a hashed password for the database credentials
When I tried to use them, I was able to login directly to their read replica RDBMS, I had access to all their customer data (including phones & home addresses)
Being the saint I am, I informed them of the ignorance made by their developer and was presented with some cool swag.5 -
I imagine those researcher must be like : "Would you give us your password? It's for a research project"
 3
3 -
My brother singed up for a browser game.... They sent him his log data (including password) via email7
-
A colleague and I spent a month building a Shopify app that allows merchants to give customers store credit.
Since Shopify's API is so limited, we were forced to augment it's functionality with a Chrome extension.
Now before you go throwing full wine bottles at your screen because of how wrong and disgusting that is, note that Shopify's official documentation recommends 5 different extensions to augment functionality in their admin panel, so as gross as it is, it seems to be the Shopify way...
Today we got a reply from their review team. They won't accept the app because it requires a Chrome extension to work properly and that is a security risk.
Are you fucking kidding me? So I guess Shopify is exempt from their own security standards. Good to know.
Not to mention the plethora of published apps that require a staff account's username and password to be provided in plain text upon setup so it can spoof a login and subsequent requests to undocumented endpoints.
Fuck you and your "security standard" Shopify! -
No, MD5 hash is not a safe way to store our users' passwords. I don't care if its been written in the past and still works. I've demonstrated how easy it is to reverse engineer and rainbow attack. I've told you your own password for the site! Now please let me fix it before someone else forces you to. We're too busy with other projects right now? Oh, ok then, I'll just be quiet and ignore our poor security. Whilst I'm busy getting on with my other work, could you figure out what we're gonna do with the tatters of our client's business (in which our company owns a stake) in the aftermath of the attack?7
-
This is from my days of running a rather large (for its time) Minecraft server. A few of our best admins were given access to the server console. For extra security, we also had a second login stage in-game using a command (in case their accounts were compromised). We even had a fairly strict password strength policy.
But all of that was defeated by a slightly too stiff SHIFT key. See, in-game commands were typed in chat, prefixed with a slash -- SHIFT+7 on German-ish keyboards. And so, when logging in, one of our head admins didn't realize his SHIFT key didn't register and proudly broadcast to the server "[Admin] username: 7login hisPasswordHere".
This was immediately noticed by the owner of a 'rival' server who was trying to copy some cool thing that we had. He jumped onto the console that he found in an nmap scan a week prior (a scan that I detected and he denied), promoted himself to admin and proceeded to wreak havoc.
I got a call, 10-ish minutes later, that "everything was literally on fire". I immediately rolled everything back (half-hourly backups ftw) and killed the console just in case.
The best part was the Skype call with that admin that followed. I wasn't too angry, but I did want him to suffer a little, so I didn't immediately tell him that we had good backups. He thought he'd brought the downfall of our server. I'm pretty sure he cried.5 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
***JUST BECAUSE SECURITY***
My father deleted the email with the credential for our ISP (pppoe: username and password), and I need it to connect a router.
Just called the tecnical service, after a couple of minutes they gave it to me.
They sent to me both username and password.
In clear.
Asking me where to send (which mail).
I DIDN'T EVEN KNOW HOW IS CALLED THE CREDENTIAL I NEED.
Obviously, I just had to say the accountholder of the bill.
Now I am super scared, i can virtually access any account.8 -
"please use a secure password*"
* But don't make it too secure, 20 Charakters is enough.
Why would you fucking do this? The only reason I can think about is a scenario like this:
"How do we store the passwords in the database?"
"Just like anything else?"
"So I create a VARCHAR(20)?"
"Yeah why not? It's good enough for a name, and you shouldn't use your or anyone else's name as a password, so it should be perfect"10 -
I have bank accounts with 5 different banks.
I HAVE TO use 4-5 different government websites.
Every fucking place: you cannot use these "~-/;^"(some others too) symbols in your password.
Are you freaking fucking kidding me!! And all of them have a limit of 12or15 characters.
If this wasn't mind numbingly stupid enough, they fucking go ahead and force you to change password every fucking month or two.
THIS IS NOT SECURITY. YOU SHOULDN'T FORCE SOMEONE TO LIMIT THERE PASSWORDS TO:
- CERTAIN CHARACTERS
- A 15 CHARACTER SIZE LIMIT
- THRN OVERTHAT, FORCE TO CHANGE PASSWPRDS PERIODICALLY.
ALL THE 5 MAJOR FUCKING BANKS IN INDIA.
FUUUUUCCCCKKKKK YOUU 🖕11 -
The tech stack at my current gig is the worst shit I’ve ever dealt with...
I can’t fucking stand programs, especially browser based programs, to open new windows. New tab, okay sure, ideally I just want the current tab I’m on to update when I click on a link.
Ticketing system: Autotask
Fucking opens up with a crappy piss poor sorting method and no proper filtering for ticket views. Nope you have to go create a fucking dashboard to parse/filter the shit you want to see. So I either have to go create a metric-arse tonne of custom ticket views and switch between them or just use the default turdburger view. Add to that that when I click on a ticket, it opens another fucking window with the ticket information. If I want to do time entry, it just feels some primal need to open another fucking window!!! Then even if I mark the ticket complete it just minimizes the goddamn second ticket window. So my jankbox-supreme PC that my company provided gets to strugglepuff along trying to keep 10 million chrome windows open. Yeah, sure 6GB of ram is great for IT work, especially when using hot steaming piles of trashjuice software!
I have to manually close these windows regularly throughout the day or the system just shits the bed and halts.
RMM tool: Continuum
This fucker takes the goddamn soggy waffle award for being utterly fucking useless. Same problem with the windows as autotask except this special snowflake likes to open a login prompt as a full-fuck-mothering-new window when we need to open a LMI rescue session!!! I need to enter a username and a password. That’s it! I don’t need a full screen window to enter credentials! FUCK!!! Btw the LMI tools only work like 70% of the time and drag ass compared to literally every other remote support tool I’ve ever used. I’ve found that it’s sometimes just faster to walk someone through enabling RDP on their system then remoting in from another system where LMI didn’t decide to be fully suicidal and just kill itself.
Our fucking chief asshat and sergeant fucknuts mcdoogal can’t fucking setup anything so the antivirus software is pushed to all client systems but everything is just set to the default site settings. Absolutely zero care or thought or effort was put forth and these gorilla spunk drinking, rimjob jockey motherfuckers sell this as a managed AntiVirus.
We use a shitty password manager than no one besides I use because there is a fully unencrypted oneNote notebook that everyone uses because fuck security right? “Sometimes it’s just faster to have the passwords at the ready without having to log into the password manager.” Chief Asshat in my first week on the job.
Not to mention that windows server is unlicensed in almost every client environment, the domain admin password is same across multiple client sites, is the same password to log into firewalls, and office 365 environments!!!
I’ve brought up tons of ways to fix these problems, but they have their heads so far up their own asses getting high on undeserved smugness since “they have been in business for almost ten years”. Like, Whoop Dee MotherFucking Doo! You have only been lucky to skate by with this dumpster fire you call a software stack, you could probably fill 10 olympic sized swimming pools to the brim with the logarrhea that flows from your gullets not only to us but also to your customers, and you won’t implement anything that is good for you, your company, or your poor clients because you take ten minutes to try and understand something new.
I’m fucking livid because I’m stuck in a position where I can’t just quit and work on my business full time. I’m married and have a 6m old baby. Between both my wife and I working we barely make ends meet and there’s absolutely zero reason that I couldn’t be providing better service to customers without having to lie through my teeth to them and I could easily support my family and be about 264826290461% happier!
But because we make so little, I can’t scrap together enough money to get Terranimbus (my startup) bootstrapped. We have zero expendable/savable income each month and it’s killing my soul. It’s so fucking frustrating knowing that a little time and some capital is all that stands between a better life for my family and I and being able to provide a better overall service out there over these kinds of shady as fuck knob gobblers.5 -
Security rant ahead - you have been warned.
It never fails to amuse and irritate me that, despite being in the 2019 supposed information age, people still don't understand or care about their security.
I've travelled to a lot of ports and a lot of countries, but, at EVERY port, without fail, there will be at least one wifi that:
- Has default name/password that has been cracked already (Thomson/SpeedTouch/Netfaster etc)
- Has a phone number as password (reduces crack time to 15-30 mins)
- Someone, to this day, has plain old WEP
I am not talking about cafeteria/store wifi but home networks. WTF people?! I can check my email (through VPN, of course) but it still bugs me. I have relented to try and snoop around the network - I can get carried away, which is bad. Still...
The speed is great though :P9 -
Customer: «We want all the users belonging to this organization share the same username and password»
[Editor's note: we are talking about 500 users, more or less half of the total in the system]
Customer, after some minutes: «It's very important for us having the web interface using HTTPS, because we care security a lot».
So, please, go fuck yourself. And die.6 -
TL;DR I'm fucking sick and tired of Devs cutting corners on security! Things can't be simply hidden a bit; security needs to be integral to your entire process and solution. Please learn from my story and be one of the good guys!
As I mentioned before my company used plain text passwords in a legacy app (was not allowed to fix it) and that we finally moved away from it. A big win! However not the end of our issues.
Those Idiot still use hardcoded passwords in code. A practice that almost resulted in a leak of the DB admin password when we had to publish a repo for deployment purposes. Luckily I didn't search and there is something like BFG repo cleaner.
I have tried to remedy this by providing a nice library to handle all kinds of config (easy config injection) and a default json file that is always ignored by git. Although this helped a lot they still remain idiots.
The first project in another language and boom hardcoded password. Dev said I'll just remove before going live. First of all I don't believe him. Second of all I asked from history? "No a commit will be good enough..."
Last week we had to fix a leak of copyrighted contend.
How did this happen you ask? Well the secure upload field was not used because they thought that the normal one was good enough. "It's fine as long the URL to the file is not published. Besides now we can also use it to upload files that need to be published here"
This is so fucking stupid on so many levels. NEVER MIX SECURE AND INSECURE CONTENT it is confusing and hard to maintain. Hiding behind a URL that thousands of people have access to is also not going to work. We have the proof now...
Will they learn? Maybe for a short while but I remain sceptic. I hope a few DevrRanters do!7 -
Security for 2017: Because SSL has nothing to do with security, and just Google's way of increasing it's monopoly...
 18
18 -
So I thought I will set up a PIN to make logging into the corporate PC easier. Hm... based on these requirements I can probably stick with password.
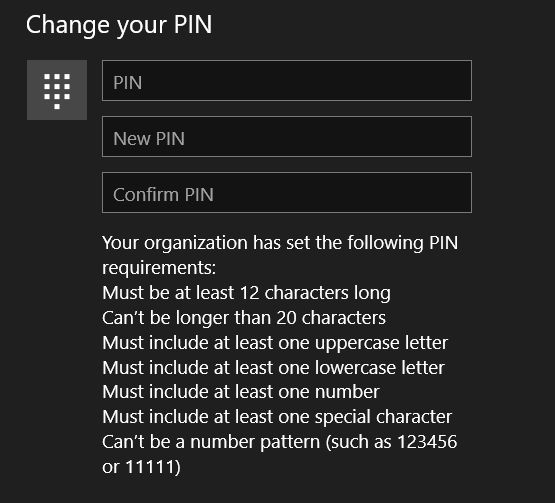 12
12 -
M - Me
F - Family member
F: So you study computer science... Could you recover my Gmail login data? I don't remember my email address, password or security question. (7th request to me like that from the same person, they don't bother to write down the recovered pw)
M: I can't do it if I don't know any of the above
F: Wow, I thought you're a good student... Could you at least create a new account for me?
M: But you won't even remember the new... [gets interrupted]
F: So, are you going to talk trash or get to work? You would have already been 50% done
PLEASE I'M SO TIRED OF IT. HOW DO I DEAL WITH THESE OTHER THAN TELLING THEM WHAT I THINK ABOUT THEM. I SEEK HELP12 -
Something I probably shouldn't talk about:
One of the projects at work has a specific path you can visit. The """security""" is that nobody should know the path. But I can guaran-fucking-tee you it's not difficult to guess.
On this page, ***without a login***, you can view some user information. Well, you can view all of it, but only certain fields.
And if you perform a specific action on this page, you can get their password, plaintext.
This project is not mine. But learning all of this made me super uneasy. I had to share it.14 -
Translation: “The Password is to long. Please choose a Password that is not longer than 12 Characters.”
Oh, and the Password can only contain Letters and numbers 🙃 14
14 -
Doing some Christmas shopping.
Creating some throwaway accounts in various e-shops
Some e-shops send me my password via email upon registration.
I've spent the better half of a day emailing those e-shops to revise their IT security policies.
Haven't bought a single gift yet.
Time well spent!6 -
Switched banks, got new e-banking, unable to set up a new password.
It contains invalid characters.
IT'S A FUCKING BANK ACCOUNT I SHOULD BE ABLE TO USE HASHTAGS OR EVEN HAVE FUCKING SPACES IN IT IF I FEEL LIKE IT.7 -
Getting real fucking sick of shitty websites excessive security measures!
1. Username
2. Password
3. Captcha
4. Mandatory 2FA
We don't recognize your IP, please log into your email, click the link, get redirected and complete steps 1-4 again! Also the site will time out in 10 minutes if you aren't actively using it. Have a nice day!
Go fuck yourself.7 -
One of our newly-joined junior sysadmin left a pre-production server SSH session open. Being the responsible senior (pun intended) to teach them the value of security of production (or near production, for that matter) systems, I typed in sudo rm --recursive --no-preserve-root --force / on the terminal session (I didn't hit the Enter / Return key) and left it there. The person took longer to return and the screen went to sleep. I went back to my desk and took a backup image of the machine just in case the unexpected happened.
On returning from wherever they had gone, the person hits enter / return to wake the system (they didn't even have a password-on-wake policy set up on the machine). The SSH session was stil there, the machine accepted the command and started working. This person didn't even look at the session and just navigated away elsewhere (probably to get back to work on the script they were working on).
Five minutes passes by, I get the first monitoring alert saying the server is not responding. I hoped that this person would be responsible enough to check the monitoring alerts since they had a SSH session on the machine.
Seven minutes : other dependent services on the machine start complaining that the instance is unreachable.
I assign the monitoring alert to the person of the day. They come running to me saying that they can't reach the instance but the instance is listed on the inventory list. I ask them to show me the specific terminal that ran the rm -rf command. They get the beautiful realization of the day. They freak the hell out to the point that they ask me, "Am I fired?". I reply, "You should probably ask your manager".
Lesson learnt the hard-way. I gave them a good understanding on what happened and explained the implications on what would have happened had this exact same scenario happened outside the office giving access to an outsider. I explained about why people in _our_ domain should care about security above all else.
There was a good 30+ minute downtime of the instance before I admitted that I had a backup and restored it (after the whole lecture). It wasn't critical since the environment was not user-facing and didn't have any critical data.
Since then we've been at this together - warning engineers when they leave their machines open and taking security lecture / sessions / workshops for new recruits (anyone who joins engineering).26 -
Sometimes I wonder how compromised my parents online security would be without my intervention.
My mom logged into her gmail and there was an red bar on top informing about Google preventing an attempted login from an unknown device.
Like typical parents / old people, that red bar didn't caught her attention but I noticed it immediately. I took over and looked into it. It showed an IP address and a location that was quite odd.
I went ahead with the Account security review and I was shocked to find that she had set her work email address as the recovery email!!
I explained her that work email accounts cannot be trusted and IT department of the workplace can easily snoop emails and other info on that email address and should not be related to personal accounts.
After fixing that issue, me being a typical skeptic and curious guy, I decided to find more info about that IP address.
I looked up the IP address on a lookup website and it showed an ISP that was related to the corporate office of her workplace. I noticed the location Google reported also matched with the corporate office location of her work.
Prior to this event, few days ago, I had made her change her gmail account password to a more secure one. ( Her previous password was her name followed by birth date!! ). This must have sent a notification to the recovery mail address.
All these events are connected. It is very obvious that someone at corporate office goes through employees email addresses and maybe even abuse those information.
My initial skeptism of someone snooping throguh work email addresses was right.
You're welcome mom!9 -
Microsoft brute-forces password-protected archives in OneDrive.
“Microsoft will decrypt, open, and scan protected Zip archives uploaded to the company's cloud servers in search of potential computer threats. Security researcher Andrew Brandt recently discovered the issue while trying to share malware samples with other researchers through SharePoint.”
This is when I encrypt my archives, I use _very_ long passwords generated by Bitwarden. Like this: qkYdE5i@27yHTTj8YsMDKQ9^mo$j@!P^M4qA95Y5VqR*53otAMuMv$9sdxtF4HAuNdAYoW9RPVxucJ3
Good luck bruteforcing that, Microsoft!
https://techspot.com/news/... 14
14 -
Client: why do I have to use such a hard password for this website?
Me: For security reasons to protect your content and identity of your clients.
Client: Can't you just use the password that I'm used to? I use it on my banking software, and I've never been hacked so it should be good enough for you!
Me: what's the password that you want me to set up for you?
Client: you ready to take it down?
Me: go ahead.
Client: T ... U ... R ... D. You got that?
Me: ... Yes ...
*sigh*6 -
I just had to print out some bills for a colleague.
Nothing too bad you say?
Well.. She doesn't seem to care about security or privacy at all.
I opened the website of her email provider at my computer and moved away from the keyboard, so she could log in.
But instead she told me her email and password... In an office with some other colleagues... Multiple times and wrote it onto a piece of paper that the later left on my table.
After that I should look through her inbox to find the bills.
(Yup, I know a lot more about her now)
After finding and printing out her bills, she just thanked me and walked out of the office, because hey, why should I log out of her account?
It's nice that she trusts me... But that was a bit too much...4 -
My argument: Password change policies (every 3, 6 moths, etc.) are a detriment to security because users will either come up with simple, throw-away passwords (knowing they will need to change them soon anyways) or use the same password anyways with a few variations.
Discuss.22 -
Oh the irony: one of the e-banks I use, forces users to type their passwords via virtual on screen keyboard (javascript based!!!) due to security 'standards' yet in the same breath doesn't allow a user to use any other character for password besides the basic alfanum.. o.O fml4
-
Finally got a new job, but it's already a horror story not even 2 hours in (making this while on break)
Everyone here is an Intern, IT? Interns, Designers? Interns, HR? Interns.
The Person who I should've worked with got fired yesterday, and now I have to work all of his shit up from 0, Documentation? Fragmental, a few things here and there, but nothing really.
IT security also doesn't exist in the slightest, there is an Excel sheet called "Master_Passwords" and every single password is in Plaintext, written out for everyone to see. (at least they used "strong" passwords)
And the place also looks run down, theres PC's, Laptops, Mics, Cables etc. lying literally everywhere no-one knows what works and what doesn't (since everyone is an intern)
Not to mention the "Server Room" is an absolute mess itself, cables hanging from literally anywhere, powerstrips are ontop of servers, each rack has like 2 or 3 2U Servers, (in a 40u Rack) and there are 10 of them!4 -
CR: "Add x here (to y) so it fits our code standards"
> No other Y has an X. None.
CR: "Don't ever use .html_safe"
> ... Can't render html without it. Also, it's already been sanitized, literally by sanitize(), written by the security team.
CR: "Haven't seen the code yet; does X change when resetting the password?"
> The feature doesn't have or reference passwords. It doesn't touch anything even tangentially related to passwords.
> Also: GO READ THE CODE! THAT'S YOUR BLOODY JOB!
CR: "Add an 'expired?' method that returns '!active'?"
> Inactive doesn't mean expired. Yellow doesn't mean sour. There's already an 'is_expired?' method.
CR: "For logging, always use json so we can parse it. Doesn't matter if we can't read it; tools can."
CR: "For logging, never link log entries to user-readable code references; it's a security concern."
CR: "Make sure logging is human-readable and text-searchable and points back to the code."
> Confused asian guy, his hands raised.
CR: "Move this data formatting from the view into the model."
> No. Views are for formatting.
CR: "Use .html() here since you're working with html"
> .html() does not support html. It converts arrays into html.
NONE OF THIS IS USEFUL! WHY ARE YOU WASTING MY TIME IF YOU HAVEN'T EVEN READ MY CODE!?
dfjasklfagjklewrjakfljasdf5 -
Part of a product I used to work on contained a one time password generator that randomly strung together a few words from a word list.
Nothing wrong with the security, but this word list hadn't been filtered, so we did have a "bug report" from a customer who had a one time password that contained a questionable phrase:
"fucking pork Muslim"
...Call me a terrible person, but I never did get around to fixing that...3 -
Pro security tip:
Use a very simple password because h4x0rs expect a difficult one so they can't cr4ck yours8 -
What. The. Actual. Fuck.
My co-workers just tried to convince me that the following is a secure password:
"ThisIsASecurePassword2018"
Just... I mean... Why? *sigh*
Their argumentation is based on the new NIST guidelines.
If they've read these guidelines CAREFULLY though... (not only the appendix) it actually states "Don't use words from the dictionary". Passwords like these should even be rejected right away.15 -
Taking IT classes in college. The school bought us all lynda and office365 accounts but we can't use them because the classroom's network has been severed from the Active Directory server that holds our credentials. Because "hackers." (The non-IT classrooms don't have this problem, but they also don't need lynda accounts. What gives?)
So, I got bored, and irritated, so I decided to see just how secure the classroom really was.
It wasn't.
So I created a text file with the following rant and put it on the desktop of the "locked" admin account. Cheers. :)
1. don't make a show of "beefing up security" because that only makes people curious.
I'm referring of course to isolating the network. This wouldn't be a problem except:
2. don't restrict the good guys. only the bad guys.
I can't access resources for THIS CLASS that I use in THIS CLASS. That's a hassle.
It also gives me legitimate motivation to try to break your security.
3. don't secure it if you don't care. that is ALSO a hassle.
I know you don't care because you left secure boot off, no BIOS password, and nothing
stopping someone from using a different OS with fewer restrictions, or USB tethering,
or some sort malware, probably, in addition to security practices that are
wildly inconsistent, which leads me to the final and largest grievance:
4. don't give admin priveledges to an account without a password.
seriously. why would you do this? I don't understand.
you at least bothered to secure the accounts that don't even matter,
albeit with weak and publicly known passwords (that are the same on all machines),
but then you went and left the LEAST secure account with the MOST priveledges?
I could understand if it were just a single-user machine. Auto login as admin.
Lots of people do that and have a reason for it. But... no. I just... why?
anyway, don't worry, all I did was install python so I could play with scripting
during class. if that bothers you, trust me, you have much bigger problems.
I mean you no malice. just trying to help.
For real. Don't kick me out of school for being helpful. That would be unproductive.
Plus, maybe I'd be a good candidate for your cybersec track. haven't decided yet.
-- a guy who isn't very good at this and didn't have to be
have a nice day <3
oh, and I fixed the clock. you're welcome.2 -
Forgot my password at school, say so, they tell me the password. Have they never heard about security?9
-
Customer: Do you need my computer password?
Me: Yes, I do. Why don't you write it down for me? *fills out work order form while she writes down her password*
Customer: Here you go *slides me sticky note with password on it*
Me: *usual spiel about computer repair stuff*
Customer: *leaves*
Me: *to Coworker* So this lady's password is "AmishForLife* (modified for security purposes).
Coworker: On her iPad?!
Me: And her computer, yes
Coworker: *laughs*
Me: I wonder how well that's working out for her... -
Saw this security blunder a while ago. Went onto some site and it showed me this username/password dialog (probably an apache's htpasswd or nginx one). Went away but returned quickly because I noticed I could see all content. Then I thought 'why the fuck not try?' so I dragged the auth popup thingy to the side of the screen and et voila... I could interact with the page as if nothing was wrong while the authentication popup was hovering above the page on the right!
I sat there giggling dramatically for a while. -
When I get on a site that is like “your password must contain upper case, lower case, a number, a symbol”, at first I’m like ooook, security I guess I’ll generate a long password, but then they sit there and say “and be at least 6 but not more than 10 characters”
WTF you fuckers really don’t know anything do you.2 -
So at work with the Macs we use, we have some guy come in after hours to service the Macs, and that means the security risk of leaving our passwords on our desks.
Not being a fan of this I tell my boss, he knows it's a risk and despite that he doesn't want this guy coming in while we're here.
Though my main problem is the Mac guy Steve is arrogant and thinks he's a know it all, and with the software I have on the Mac may end up deleting something important, I have git repo and all but I feel off just letting someone touch my computer without me being there.
I tell my boss about the software and stuff he just says contact Steve and tell him about it, to ignore the software and such, I say alright, I write up an email telling him not to touch the software listed and the folders of software documents (again it's all backed up).
No reply, I tell my boss and he says call him, I call him and he hangs up on me on the second ring!
Not sure if he's busy, but I left him a message, asking if he got my email, no reply and it's coming close to the end of the day (going to service Macs in the weekend)
I'm just not going to leave my info because if this guy can't check emails or even get back to someone why should I bother with this bullshit of risking my work.
From all the info I hear about him and my previous rants he's an arrogant prick who loves Macs.
Can't wait to leave this company, pretty sure leaving my password on my desk is a breach of our own security policy, and since 8-9 people are doing it, it's a major risk.
But he's friends with the CEO so apparently it's fuck our own security policy.11 -
My girlfriend configuring her e-mail account in the app because her phone had to be reset to factory :
-I can't figure out how to do these setting, annoying...
-Oh yeah the imap and smtp servers can be tricky, let me put that
(I Google the settings for her mail provider and put them in)
-It still doesn't work.
-Uuuh, maybe with another security setting, try it.
-This shit still doesn't work, seriously my phone is broken.
-Have you verified the e-mail address and carefully typed the password?
-Yes of course, I've tried it several time
(I take the phone and check all the parameters... During a looooong time... Until it hits me.)
-Hmm... Can you read the e-mail you've entered?
-Yeah, it's my mail, blabla@hotmail.com.
-No can you read it again please?
-It's blabla, why?
-No, can you *spell* your e-mail?
-Yeah it's B-L-A-B-L-A-@-H-O-M-A... Ow shit...
- ¯\_(ツ)_/¯ -
This is just priceless. I submitted my thesis to an academic congress, which sent me this confirmation email. They are so 'concerned about security' that they assured me the email is legitimate by including MY PASSWORD.
 3
3 -
Sooo I've been working on an ancient php 5.6 project that did not have any documentation and was a homemade "framework" created 7 years ago. The original creator is long gone and no one else knows a lot about this project.
When I first looked into it I almost immediately noticed the security flaws...
Old outdated libraries
a "development" feature to easily turn dev mode on/off
BY A GET PARAMETER!
it spits out full sql queries and php warnings -.-
Oh and did I mention that the site is a webshop.... and has a backdoor password?
AND THAT THE CUSTOMER REQUESTED THAT?3 -
If we compare this list with last year’s list, nothing much has changed. The top three worst passwords of last year were ‘123456’, ‘password’, and ‘123456789’. Source : Splashdata
Top 10 worst passwords in 2019 below:
1. 123456
2. 123456789
3. qwerty
4. password
5. 1234567
6. 12345678
7. 12345
8. iloveyou
9. 111111
10. 12312315 -
Wow, I'm going to have a hard time remembering this one.
IT have changed after so many years the password criteria for our machines, to the point it's a bit ridiculous.
Like I'm all for securing your accounts and using random passwords but, this is rough.
Minimum of 14 chars
Not the past 6 passwords
Must contain several %}*]=[^{
Must contains numbers
Must contain upper case letters
Must contain Lower case letters
Must not end in a number
Must sacrifice a virgin on every login
Must be changed every 30 daysrant security vs usability kill me - kill me now password managers go hard or go home - oh wait i am home22 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
I had security reopen our test-user last week. I could run the tests once, then they started failing with "blocked user due to too many attempts at logging in". Huh, that's weird. I go through everything, every script, every scheduled task, every nook and cranny of every drive on every machine I could reach, and make sure the password is updated everywhere. Reopen account. Same shit.
I email around to some people, they don't use it, one guy asks if I checked x, y and z, I did. Then he's sure we don't use it anywhere else.
It's one of our fucking contractors that took one of our scripts (that they're supposed to have duplicate copies of) and forgot to change to their own credentials. That's literally the agreement, take our scripts and change the user and run them on your machines.
Afhfjdkdhdjdbd stop locking me out of everything with your incompetence. I email them, some cunt gets back to me asking for the new password. NO. USE. YOUR. OWN. CREDENTIALS. I KNOW YOU HAVE THEM, THEY'RE HERE IN THE LIST AND BEING USED IN ALL OTHER SCRIPTS AAAAAAAAAHHH6 -
So I manage multiple VPS's (including multiple on a dedicated server) and I setup a few proxy servers last week. Ordered another one yesterday to run as VPN server and I thought like 'hey, let's disable password based login for security!'. So I disabled that but the key login didn't seem to work completely yet. I did see a 'console' icon/title in the control panel at the host's site and I've seen/used those before so I thought that as the other ones I've used before all provided a web based console, I'd be fine! So le me disabled password based login and indeed, the key based login did not work yet. No panic, let's go to the web interface and click the console button!
*clicks console button*
*New windows launches.....*
I thought I would get a console window.
Nope.
The window contained temporary login details for my VPS... guess what... YES, FUCKING PASSWORD BASED. AND WHO JUST DISABLED THE FUCKING PASSWORD BASED LOGIN!?!
WHO THOUGHT IT WOULD BE A GOOD IDEA TO IMPLEMENT THIS MOTHERFUCKING GOD?!?
FUUUUUUUUUUUUUUUUUUUUUUU.3 -
Microsoft seriously hates security, first they do enforce an numer, upper and lowercase combined with a special character.
But then they allow no passwords longer than 16 characters....
After that they complain that "FuckMicrosoft!1" is a password they've seen to often, gee thanks for the brute force tips.
To add insult to injury the first displayed "tip" take a look at the attached image. rant password security security 101 security fail annoyance passwords passwords stupid practices microsoft13
rant password security security 101 security fail annoyance passwords passwords stupid practices microsoft13 -
Google has a password reset procedure so intense, that even if I can sign into my recovery account and give them the code from there, use 2 factor auth and give them the code from there, tell them my recovery phone(s) number(s), give them my mother's father's mother's late cousin twice removed daughter's maiden name, and whatever other security measures were set in place, I can't get a fucking password reset. Thanks Google, fuck you.3
-
Thanks to mandatory password change, today:
- My windows account got locked because my phone kept logging into wifi using
old password.
- Google Hangouts were silently running in background with old session until I re-opened it. Work of others delayed by 4 hours due to missing message notifications.
- Docker for Windows lost credentials needed to use SMB mounts - 1h of debugging why my containers mount empty folders ( now I will know)
- Google G-Sync for Outlook asked for new password on outlook restart - few mails delayed.
All of that for sake of security that could be easily solved with 2FA instead, not faking that "I do not change number at the end of my password" -
Clicking "forgot my password" and getting a mail with my password in clear text. Sending a mail and asking why they don't care about security. The answer I'm getting is "it's a feature, makes things easier". Yeah...3
-
Discord and captchas can go get fucked in the ass by a rusty, tetanus ridden 2m pole....
I changed my discord-password yesterday and, naturally it prompted me for a login today. So I enter my new password and that motherfucking spawn from satans anus himself with the name of captcha threw itself at me... I seriously had to select fucking street signs for about 5min before Discord let me know that I apparently logged in from a new IP (thanks VPN) and therefore needed to confirm my e-Mail address. Alright, so off to my inbox I go.
SURPRISE, I also changed my password there yesterday (LastPass Security Challenge, I changed like 30 passwords yesterday) and guess what was waiting for me?... If you guessed a captcha, you just got full fucking marks. So I was busy selecting busses and streets for the next 3min again before I could finally log into that piece of trash and autorize my IP-address and log into Discord6 -
So... did I mention I sometimes hate banks?
But I'll start at the beginning.
In the beginning, the big bang created the universe and evolution created humans, penguins, polar bea... oh well, fuck it, a couple million years fast forward...
Your trusted, local flightless bird walks into a bank to open an account. This, on its own, was a mistake, but opening an online bank account as a minor (which I was before I turned 18, because that was how things worked) was not that easy at the time.
So, yours truly of course signs a contract, binding me to follow the BSI Grundschutz (A basic security standard in Germany, it's not a law, but part of some contracts. It contains basic security advice like "don't run unknown software, install antivirus/firewall, use strong passwords", so it's just a basic prototype for a security policy).
The copy provided with my contract states a minimum password length of 8 (somewhat reasonable if you don't limit yourself to alphanumeric, include the entire UTF 8 standard and so on).
The bank's online banking password length is limited to 5 characters. So... fuck the contract, huh?
Calling support, they claimed that it is a "technical neccessity" (I never state my job when calling a support line. The more skilled people on the other hand notice it sooner or later, the others - why bother telling them) and that it is "stored encrypted". Why they use a nonstandard way of storing and encrypting it and making it that easy to brute-force it... no idea.
However, after three login attempts, the account is blocked, so a brute force attack turns into a DOS attack.
And since the only way to unblock it is to physically appear in a branch, you just would need to hit a couple thousand accounts in a neighbourhood (not a lot if you use bots and know a thing or two about the syntax of IBAN numbers) and fill up all the branches with lots of potential hostages for your planned heist or terrorist attack. Quite useful.
So, after getting nowhere with the support - After suggesting to change my username to something cryptic and insisting that their homegrown, 2FA would prevent attacks. Unless someone would login (which worked without 2FA because the 2FA only is used when moving money), report the card missing, request a new one to a different address and log in with that. Which, you know, is quite likely to happen and be blamed on the customer.
So... I went to cancel my account there - seeing as I could not fulfill my contract as a customer. I've signed to use a minimum password length of 8. I can only use a password length of 5.
Contract void. Sometimes, I love dealing with idiots.
And these people are in charge of billions of money, stock and assets. I think I'll move to... idk, Antarctica?4 -
For security reasons and to have stronger passwords, my organization enforces us to use '@123' at the end of the password!! Dumb motherfuckers!! :P2
-
Had my hairdresser tell me she thought her phone number was a great password for all her online accounts.
Just smiled and nodded, I feel there’s a time and a place for lectures on internet security.11 -
auto.self.whatever.rant()
A few years ago, we had a lesson on git and stuff, and we had to create our first repository and push something on it to get familiar with the thing.
Our teacher jokingly said at the end "And always remember, no password in a repository!", and I thought to myself "who can be dumb enough to do actually do something like that?"
Now, guess which piece of shit had to reinstall two of his fucking servers because of security issues coming from not one but github repositories?4 -
So our teacher just has us sign up for a learning site called Gizmos with a ton of students information. A lot of students forgot their password as always and some didn't register with an email so I expected the teacher to reset them..
Then the teacher had students come up to the front of the f****** class and SHOWED THEM THEIR PASSWORD IN PLAIN TEXT. WHAT THE HELL3 -
Tl;dr stupid password requirements
Begin quote
Password must not contain any non-alphanumeric characters.
Your Password change was not accepted. Enter your current Password correctly following the rules for New Passwords. Please try again.
Passwords must be between 8 and 12 characters in length and MUST contain each of the following:
At least 1 lower case character (a-z)
At least 1 upper case character (A-Z)
At least 1 numeric digit (0-9)
But, MUST NOT contain:
more than five repeating characters in a row (e.g. 111111356 would not be valid, but 112233445 would be valid)
spaces or other special characters
NOTE: Your new password cannot be the same as any of your 10 previous passwords.
End quote
Are you fucking kidding me? Only (26+26+10)^8 through
(26+26+10)^12 different passwords to go through? It's like the oxygen wasters that built this website give zero fucks about security.
Why? This is the site that manages money and investments. Just allow passwords up to 64 characters, allow any ascii character and just fucking encod the characters to prevent any Injunction.4 -
Why the Fuck is PayPal only allowing passwords up to 20 characters . Even the most useless websites aren't doing that (at least not visisible, maybe they shorten it in the backend).10
-
Security Horror Story:
A password authenticator which is case-insensitive and all special characters are treated as the same value. As a bonus, all passwords are truncated to 4 characters.2 -
Fuck your clients, right...? A small town bank I’m doing some security work for; I had them create me a test account. I received an email with my password; are you fucking serious...?3
-
I found this old printout of my username and password for my school account from ca 2008. I really like how the password are the same as the username except for some capitalization 😂😅
“sECurItY” 10
10 -
I don't usually look at the "updates" section of my Gmail but yesterday I did. One message cought my eye: "Your application to Microsoft BizSpark has been approved" but I've never applied to Microsoft BizSpark!
Someone has registered in my name, opened a Microsoft Outlook account under my full name and added my startup details for applying to BizSpark! One issue though, he used some Spanish equivalent of mailinator to subscribe so I could easily reset the password and replace the security email. Now I have 5 visual studio subscriptions I don't know what to do with.5 -
Not a Story about an actual hack, but a story about people being dumb and using hacks as an excuse.
A few weeks ago my little cousin would reach out to me because "his Account was hacked...". Supposedly his League of Legends account was hacked by a guy of his own age (14) and this guy was boasting about it.
So i asked the usual things: "Has the email account been hijacked? Did anyone know about details to your acvount access? Etc..."
Turns out that one if his "friends" knew his password and username, but suppsedly erased these Informationen. And that was the part i didn't buy.
This was the point where he lost. Just because i am a programmer does not mean i can retrieve an account he lost because of a dumb mistake that could have easily been avoided. And that guy who was boasting about hacking LoL Account was coincidentally freinds with the friend who had the user credentials and password.
Moral of the Story? The biggest security weakness is almost always the user or a human in between... -
This is not fucking security, it's obscurity! What the fuck is a memorable word without any context! It drives me up the fucking wall. This doesnt help anyone it just promotes people to put silly shit like password or something so they won't forget but it just makes their account weaker.
 16
16 -
IT security calls to tell me my new password, because it is poor practice to send it over encrypted message.
New password = password
I'm glad we are taking security so seriously!2 -
So today I found a way to break into any Apple Mac (provided the exploit hasn't been fixed by the owner) and access all private files, as long as I have physical access to it, in less than 5 minutes.
After finding this, a quick Google on the method reveals this has been a workaround for years.
And to think I once praised Apple for their security standards.
Edit: this was done to an in-house Mac that my company own, and had been password locked by a member of staff who had been fired, but held important company documents on the computer. It was in no way a breach of privacy.7 -
Hey Citrix:
FUCK YOU.
Learn to make an accessible log in page you fucks.
Maybe instead of vague fucking "you're user name and password is wrong" say things like "your account is locked because we somehow decided we don't like your password anymore. . . . without telling you"
Fucking 2 hours of my day wasted trying to log into my company's VM because first it wouldn't take my password (that I've had for over a month and doesn't expire for another month) over and over again. I changed it, logged in. Got up to do something that'd take less than 5 minutes. And OF COURSE the people who set up the VM made them log you out if you're gone for more than 3 minutes (fuck that guy too). Come back to a log in screen and it won't accept my new password.
Change it again. Except this time it won't accept my new password because it's "like my old password." It is in that it uses the alphabet and numbers, but it's also different in that those alphanumeric characters are LITERALLY DIFFERENT IN EVERY PLACE. I finally get it to accept a new password.
I'm also loving the whole "answer these security questions that literally anyone who does minimal research on you can answer" before I get to change my password. Yeah. Because finding my mother's maiden name or the city I was born in is so fucking hard. Literally impossible to find out what my Dad's dad's name is. Shit like that isn't publically available. Nope. Why the fuck are we still using "security" questions?
I log into Citrix again. And it takes me to . . . the log in for Citrix.
There is no word in elvish, entish or the tongues of men for this stupidity.
Fuck Citrix. Fuck the people behind the password manager (Aviator or something like that), and fuck whatever administrator setting turns my computer off due to inactivity in such a stupid short amount of time. 10 minutes, 15 minutes, that'd be fine. But it's more like 3 or 5, like wtf.2 -
A coworker told me this a little while ago and I cringed.
"Coworker installs windows partition o n a Mac, not sure what utility he used but he's handled every IT issue, people in our company for years but googling and researching ways to do things.
Steve comes along to do a service on the Macs (apparently) and sees what my coworker did and says "get rid of that it's a security risk", coworker had a legitimate reason to use Windows, plugin for Excel only works in Windows, so Steve could have totally done checks to ensure security wasn't a risk, but he's a Mac elitist, what can you do :/, lucky coworker though gets to use a windows PC and never looked back xD."
Honestly scared of Steve doing that so called service seeing I have tons of things I need to use (source tree, Android studio, some tools to test push notifications) and just down right deleting them because of his reasons, that and the whole he does services after hours without much warning (last time it was a leave password on desk for the next "week" and Steve will come in and fix the Macs) I can't defend my argument of why I use something like Android studio (to develop the app for the company LOL) -
I think I finally found a reason to have a phone with 8GB of RAM.
So that when TWRP craps out on data decryption and decides not even to ask for a password, at least I can push a whole fucking ROM into RAM to unfuck the phone. Because why not?! Why on Earth would software work properly when you can just throw more hardware at it?
Long live FBE, TWRP what craps out on it, and you remember those things.. SD cards for data storage? I could've used an unencrypted SD card so fucking badly right now, you know... Long live soldered in storage that's encrypted, "for security". Except for when the person who owns said data actually wants to use the bloody data.
FUCK!2 -
Security lifehacks 101
Why pay for password managers? Just use one secure password for every service you use! Password managers are really designed for fools who don’t know that you can just use one password for every service and who are ready to pay for that shit.
The best practice is to use your name starting with a capital letter + your main credit card number + CVC code from the back of that card as your go-to password. It’s long and hard to bruteforce and you can remember everything that way! You just need to remember that one password and you’ll always remember your payment info! No need for apple’s bad Apple Pay which is not so secure after all like everything else that Apple offers.19 -
I know folks do their best, but come on Apple, this can't be that hard. Bought an IPhone at an estate sale (elderly individual died suddenly, so no one had knowledge of the apple id, passwords, etc) and I've been trying to convince apple to clear the activation lock. (AS = Apple Support)
<after explaining the situation>
AS: "Have you tried putting the phone in recovery mode? That should clear the lock"
Me: "I've already done that. It prompts for the apple id and password, which I don't have"
AS: "You need to talk to the owner and get the information"
Me: "As I explained, I purchased the phone at an estate sale of someone who died. I have the bill of sale, serial number, the box, obituary. What else do you need?"
AS: "Have you tried contacting a family member? They might have have that information."
Me: "The family members at the sale told us this is all they had. This kind of thing has to happen. I can't believe Apple can't clear the activation lock."
AS: "Yes, we can, but I'm very sorry we take security seriously."
Me: "I understand, what do I do now?"
AS: "Did you log out of the phone? Go to settings ..."
Me: "Yes, I tried all those steps before calling. It prompts for the AppleID and password."
AS: "Did you try entering the password?"
Me: "No, I don't have it. I already explained there is no way to know"
AS: "Yes..yes...sorry...I'm just reading the information in front of me. I found something, have you tried submitting a activation lock removal request?"
Me: "Yes, it was denied, didn't tell me why, which is why I'm calling. What about taking this phone to an Apple store? I have all the paperwork."
AS: "Sure, you can try. You might need the death certificate. The family or the coroner will have a copy."
Me: "What!? Apple requires a death certificate to unlock a phone!? I'm pretty sure not even the family is going to give a total stranger a death certificate"
AS: "Sorry sir, I'm just reading what is in front of me. Without that certificate, there is no way to prove the person died. You can try the Apple store, but they will likely require it."
Me: "That's a lot of drama for unlocking a phone. A *phone*"
AS: "Yes sir, I understand. If there anything else we can do let us know and thank you for being an a apple customer."
Next stop, the Apple Store.12 -
I wanna make you feel what you have brought into my house!!
I was working with security cameras once in a home automation project. One of those camera particularly stand out by offering a cgi without password request to view and change the current passwort and username.
Seriously wtf is wrong with you? I mean this thing automatically connects to an internet service offering everyone to connect to it with that passwort and username. And I know some of you might say "hey chill the cgi is only available on the wifi" - dammit no. Security is a lifestyle do it complete or get the fuck out. God knows what other mistakes there might be hidden in that thing screaming out to everyone to watch me taking a shit.
But that's not the end of it. My company arranged a call to the technical support of that camera so that I can explain the problem and a patch gets released. Those guys didn't give a shit about it and were even laughing at me. Fuck you!
So whoever is responsible - I will find you - and you will never see me coming.4 -
Since we are using the same password on all our servers (both QA and Production environment) my team somehow decided that it would be easier to copy the private SSH key for to ALL servers and add the public key to the authorized.keys file.
This way we SSH without password and easily add it to new servers, it also means that anyone who gets into one server can get to all of them.
I wasn't a fan of the same password on all servers, but this private key copying is just going against basic security principles.
Do they want rogue connections? Because that's how you get them.1 -
“Passwords are like underwear. You shouldn’t leave them out where people can see them. You should change them regularly. And you shouldn’t loan them out to strangers.”24
-
Our new COO has decided to migrate our passwords from to a new password manager (due to security concerns).
But now, nearly 75% of our passwords are just 'missing' and we don't have access anymore to our first password manager and it's been emptied out.
AFAIK, the COO still has all the passwords but not shared. He is not responding to my mails / team message from the past day.10 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
tldr; Windows security sucks. You as a org-admin cant do anything about it. Encrypt your device. Disable USB Live boot in the bios and protect it with a STRONG password.
First of i just want to say that i DO NOT want to start the good ol' Linux VS Windows debate. I'm just ranting about Windows Security here...
Second, here's why i did all of this. I did all of this mainly becuase i wanted to install some programs on my laptop but also to prove that you can't lock down a Windows pc. I don't recomend doing this since this is against the contract i signed.
So when i got my Laptop from my school i wanted to install some programs on it, sush as VS Code and Spotify. They were not avalible in the 'Software Center' so i had to find another way. Since this was when we still used Windows 7 it was quite easy to turn sticky keys in to a command prompt. I did it this way (https://github.com/olback/...). I decided to write a tutorial while i was at it becuase i didn't find any online using this exact method. I couldn't boot from a USB cause it's disabled in the bios wich is protected by a password. Okey, Sticky keys are now CMD. So let's spam SHIFT 5 times before i log in? Yeah, thanks for the command promt. Running 'whoami' returned 'NT SYSTEM'. Apparantly NT System has domain administator rights wich allowed me to make me an Administrator on the machine. So i installed Everything i wanted, Everything was fine untill it was time to migrate to a new domain. It failed of course. So i handed my Laptop to the IT retards (No offense to people working in IT and managing orgs) and got it back the day after, With Windows 10. Windows 10 is not really a problem, i don't mind it. The thing is, i can't use any of the usual Sticky keys to CMD methods since they're all fixed in W10. So what did i do? Moved the Laptop disk to my main PC and copied cmd.exe to sethc.exe. And there we go again. CMD running as NT System on Windows 10. Made myself admin again, installed Everything i needed. Then i wanted to change my wallpaper and lockscreen, had to turn to PowerShell for this since ALL settings are managed by my School. After some messing arround everything is as i want it now.
'Oh this isnt a problem bla bla bla'. Yes, this is a problem. If someone gets physical access your PC/Laptop they can gain access to Everything on it. They can change your password on it since the command promt is running as NT SYSTEM. So please, protect your data and other private information you have on your pc. Encypt your machine and disable USB Live boot.
Have a good wekend!
*With exceptions for spelling errors and horrible grammar.4 -
This is the last part of the series
(3 of 3) Credentials everywhere; like literally.
I worked for a company that made an authentication system. In a way it was ahead of it's time as it was an attempt at single sign on before we had industry standards but it was not something that had not been done before.
This security system targeted 3rd party websites. Here is where it went wrong. There was a "save" implementation where users where redirected to the authentication system and back.
However for fear of being to hard to implement they made a second method that simply required the third party site to put up a login form on their site and push the input on to the endpoint of the authentication system. This method was provided with sample code and the only solution that was ever pushed.
So users where trained to leave their credentials wherever they saw the products logo; awesome candidates for phishing. Most of the sites didn't have TLS/SSL. And the system stored the password as pain text right next to the email and birth date making the incompetence complete.
The reason for plain text password was so people could recover there password. Like just call the company convincingly frustrated and you can get them to send you the password.1 -
TL;DR: Google asked me to PROVIDE a phone number to verify connection from a new device, on the said device.
Yesterdayto log into my work Google account from my personal laptop to check emails, calendars update and so on. I opened up a private navigation window, went to Google sign-in page, entered my credentials, all is well.
Google then decided to "verify it's me" and prompted me to PROVIDE a phone number (work account without work phone means no phone number set up) so that they can send a verification code to the number I just provided to make sure the connection is legit.
Didn't want to do that, clicked "use another method" and got asked to fill the last password I remember, which would be my current password thanks to my trusty password manager. After submitting, I'm prompted with an error saying I have to contact my admin to reset my password because they can't log me in with my CURRENT password.
I ain't gonna do that, so went back to login page, provided my phone number, got the code, filled in the code, next thing I know I'm browsing through my emails.
What the duck? Could have been anybody giving any phone number. So much for extra security.
Also don't care that they have my phone number, the issue is more about the way used to obtain it: locking me out of my account and having no other way of logging in.6 -
TL:DR
Why do so shitty "API"s exist that are even harder to write than proper ones? D:
Trying to hack my venilation at home.
This API is so horrible D:
The API is only based on POST requests no matter if you want to write values or get values and the response only contains XML with cryptic values like:
<?xml version="1.0" encoding="UTF-8"?>
<PARAMETER>
<LANG>de</LANG>
<ID>v01306</ID>
<VA>00011100000000000000000010000001</VA>
<ID>v00024</ID>
<VA>0</VA>
<ID>v00033</ID>
<VA>2</VA>
<ID>v00037</ID>
<VA>0</VA>
Also there are multiple API routes like
POST /data/werte1.xml
POST /data/werte2.xml
POST /data/werte3.xml
POST /data/werte4.xml
And actually the real API route is only given in the request body and not in the path.
Why is this so shitty? D:<
Btw in terms of security this is also top notch. It just globally saves if one computer sends the login password.
I mean why even ask for a password then? D:
That made me end up with a cronjob to send a login request so I don't have to login on any device.
PS:
You see, great piece of German engineering.3 -
Today my fellow @EaZyCode found out a local Hosting Provider has a massive security breach.
He wrote an Plugin for Minecraft with an own file explorer and the ability to execute runtime commands over it.
We discovered that this specific hosting provider stores the ftp passwords one level above the FTP-Root. In FUCKING PLAIN TEXT! AND THE MYSQL PASSWORD TOO! And even more shit is stored there ready to be viewed by intelligent people...
It's one of the fucking biggest Hosting provider Germanys!
But, because EaZyCode has such a great mind and always find such bugs, I give him the title "Providers Endboss" today, he has earned it.
Loving you ❤️
Edit: we used SendMail with runtime commands and sended too many empty Spammails (regret noting)18 -
Acquaintance of mine brags that he made a "Facebook password cracker" that took less than 30 lines of code.
I take a look at it, then I realize it's brute force password cracking.
Oh dear.
Facebook doesn't even let you do that many password attempts, not to mention that brute forcing passwords is going to take more time than the expected lifetime of the sun. (exaggeration? Maybe. But you get my point.)
Why are we still here? Just to suffer?6 -
So I just started a part time job in a hospital research center - because the processing is long I got a temporary user name and password (that belong to the main HR secretary) so I can start work straight away (mainly data analytics)
The kick?
Administrator privileges.
I can access edit create or delete everything in the entire fucking database. On my first God damn day.
In the 2nd largest hospital in the fucking country.
Agh. How do systems survive with so many dumb security breaches?4 -
half day gone try to find or remember the password of some SSL/key/encrypt/crt/shit/whatever.
Blaming myself for hours, how could I not save the password somewhere?
#Enter Password:
(I pressed enter, no password).
it works.
I love IT security -
Why the fuck do people not change their router admin password!? I was at a hotel today and could access their router admin interface with the default credentials. I guess this isn't purely the fault of the hotel because not all people know a damn thing about security and only use the interface to change the SSID and password of the AP. But why allow them to leave the default password? Why isn't this a standard feature to be forced to change the password :|12
-
Creating username / password first time - checked
Storing password in plaintext - checked
Messaging password in plain text after a password change - whaaattt???? 7
7 -
Probably the worst security I've ever seen is a website I used to visit that had their "Forgot your password?" system change the password of the account to the user's username and didn't even send an email confirmation before doing it.3
-
Fuck Monday and SAs... Just arrived at office and logged in:
Consider changing your password:
**Ok... Enters new password**
We're sorry your password is invalid
?????
Let's I already have a lower, uppercase letter, a number
....
Adds a symbol
**works**
Difference in security though? 0.... But now I have one more thing too remember...4 -
Apple: this AppleID has been locked for security reasons.
User: Sign Out
Apple: Enter the Apple ID password to turn off Find My iPhone.
User: Turn Off
Apple: You must enter both your Apple ID and password.
User: OK
Apple, please stop bugging me, all I need is to test my websites on Safari occasionally because some customers prefer to use iPhone. Just don't bother me with your Apple ID crap5 -
If your site only supports alpha numeric characters in my password. You should tell me that when I reset my password rather than just killing the special characters out of the string and submitting my password like that. I spent 15 minutes trying to log in before I gave up and reset it to something simple.
Also, you should let me use special characters in my password, it's 2017.8 -
tldr: Fuck Apple AND Microsoft...
Tried to check my "me" email today (iCloud)... and well it's apparently "locked" for god only knows what reason, and they will only let me recover it through a Hotmail account that I haven't used in >10years.. So I tried that and after one login attempt outlook.com is telling me "you've entered too many wrong password attempts, you must reset your password"... ugh OK, so I hit the button and it's asking me "my" security question.. 'where did you and your spouse meet?'.. wtf? I'm not married now nor was I @12yrs old when I made this account....
Well thanks so I guess that's fucked for forever...7 -
Saw a classmate returning an plain text password from a function to try to push it in a JSON file for an API we have to build for class.
I try to correct him and show him a few things that are better practices and for security, I get yelled at and called a know-it-all for trying to help... I'm so done with people -.-4 -
We developed this website plus custom CMS for an university. I told them that we could host the entire system and take care of it for an annual fee but they decided to host it in house because security. The IT guy didn't ask for my public key, he sent me a password. By email. Less than 8 characters long. Only recognizable abbreviated words. And a dot.3
-
this just happened a few seconds ago and I am just laughing at the pathetic site that is Facebook. xD
4 years ago:
So I was quite a noobie gamer/hacker(sort of) back then and i had a habit of having multiple gmail/fb accounts, just for gaming, like accounts through which i can log in all at once in the same poker room, so 4/5 players in the game are me, or just some multiple accounts for clash of clans for donations.
I had 7-8 accounts back then. one had a name that translated to "may the dead remain in peace "@yahoomail.com . it was linked to fb using same initials. after sometime only this and 2 of my main accs were all i cared about.even today when i feel like playing, i sometimes use those accs.
2 years ago.
My dad is a simple man and was quite naive to modern techs and used to hang around with physical button nokia phones.But we had a business change, my father was now in a partnership in a restaurant where his daily work included a lot of sitting job and and casual working. So he bought a smartphone for some time pass.
He now wanted to download apps and me to teach him.I tried a lot to get him his own acc, but he couldn't remember his login credentials.
so at the end i added one of my own fake ID's(maythedead...) so he could install from playstore, watch vids on youtube and whatever.
The Actual Adventure starts now
Today, 1 hour ago:
I had completely forgot about this incident, since my parents are now quite modern in terms of tech.
But today out of nowhere i recieved an email that someone has JUST CHAINGED MY FB PASSWORD FOR ONE OF MY FAKE ACCS!?!??
what the hell, i know it was just a useless acc and i never even check my fb from any acc these days, but if someone could login into that acc, its not very difficult to track my main accs, id's, etc so i immediately opened this fb security portal and that's where the stupidity starts:
1)To recover your account they FUCKIN ASKS FOR A PHYSICAL ID. yeah, no email, no security question you have to scan your driving license or passport to get back to your account.And where would I get a license for some person named "may the dead remain in peace"? i simply went back.
2) tried another hack that i thought that will work.Closed fb help page, opened fb again , tried to login with my old credentials, it says" old password has been changed,please enter new password", i click forget password and they send an otp. i thought yes i won, because the number and recover mail id was mine only so i received it.
when i added the otp, i was first sent to a password change page (woohoo, i really won! :)) but then it sends me again to the same fuckin physical id verification page.FFFFFFFFFuck
3)I was sad and terrified that i got hacked.But 10 mins later a mail comes ,"Your Facebook password was reset using the email address on Tuesday, April 10, 2018 at 8:24pm (UTC+05:30)."
I tried clicking the links attached, hoping that the password i changed(point<2>) has actually done something to account.NADA, the account still needs a physical license to open:/
4) lost, i just login to my main account and lookup for my lost fake account. the fun part:my account has the display pic of my father?!!?!
So apparently, my father wanted to try facebook, he used the fake account i gave him to create one, fb showed him that this id already has an fb account attached to it and he accidently changed my password.MY FATHER WAS THE HACKER THE WHOLE TIME xD.
but response from fb?" well sir, if you want your virtually shitty account back , you first will have to provide us with all details of your bank transactions or your voter id card, maybe trump will like it"
-
Security fail here. I've just started a PPI claim and have been provided a link to a so called "very secure" client area.
There are no username or passwords and the screenshot is not a first time sign up screen.
All I need to login is a surname, postcode and DOB - all information easy enough to find online.
Pretty bad IMO, esp, so considering the effort required to add a proper login using a username/password combination.
I mean I'm logged in now and have no option to set an account password :| 3
3 -
A lot of larger companies seem to be a happy about forcing employees to change their password every three months or so. They do it for security measures so that it is more difficult to break through the system, however most people end up making the worst passwords.
Instead of forcing a very good password on them every year or two maybe, they all end up having passwords like: "Summer16", "Qwer1234", "London15".
I used to work for our national police, and this was the case there as well...7 -
*follow-up to https://devrant.com/rants/1887422*
The burnt remnants of my ID card's authentication information, waiting for the wind to come pick it up. It's stored in my password database now and committed to my git server, as it should be. Storing PIN and PUK codes on paper, whatever government cunt thought thought that that was a good idea...
If you've got identification papers containing authentication information like PIN and PUK codes, by all means add them to your password manager (if you're using Linux, I'd like to recommend GNU Pass) at once and burn the physical version. There's no reason why you'd want those on paper, unless you store your passwords on a post-it too.
At least that's as much as me and possibly you as citizens can do. Our governments are doomed anyway, given the shitty security policy they have, and likely the many COBOL mainframes still in use today. Honestly, the meddlings of Russia with the US elections doesn't seem too far-fetched, given this status quo. It actually surprises me that this kind of stuff doesn't happen more often, given that certain governments hire private pentesters yet can't secure their own infrastructure.
-
A swedish insurance company has two different solution for logging in to their system.
1. An advanced high security single sign on solution involving active directory, verification of the network the request came from etc etc.
2. Using a link and passing your credentials in the query string!!! Like: insurancecompany.com?username=admin&password=password.
Solution 2 works with admin accounts from anywhere.4 -
So, I just created an account on a premium objective information website. It basically sells access to several articles on laws and general "financial relevant subjects". It is important for my work and they have pretty strict password requirements, with minimum: 18 characters length, 2 HC, 2 LC, 2 special, 2 numbers.
Without thinking twice, openned Keepass and generated a 64 length password, used it, saved it. All's good. They then unlocked my access and... wrong password. I try again... wrong password.
Thinking to myself: "No, it can't be that, maybe I only copied a portion of the password or something, let me check on CopyQ to see what password I actually used."
Nope, the password is indeed correct.
Copy the first 32 characters of the password, try it... it works...
yeah, they limit password length to 32 characters and do not mention it anywhere ... and allow you to use whatever length you want... "Just truncate it, its fine"1 -
Omg how stupid some people are... Today at my university I used the first time one of the computers in the computer room and there is a portable Firefox installed in a shared space on the computer and that is also where it saved settings etc. So this is the same for every user on that particular computer.
And when I checked the security settings I found that about 10 different accounts were saved and accessible with website username and password.
So of course the shared space Firefox is bad, but you still shouldn't save you password on a public computer :S
PS: If anyone needs a webmail account or an account for the german university network contact me :P4 -
My university has a internal developed system, where everything is managed from e-mails, exams to personal data.
What I'd like most about it, they talk all day about Internet Security and store our passwords in plain text and if you press the "I've forgott my Password button", they even send your password unencrypted, plaintext via e-mail. (Hello Wiresharks)
I don't know how to feel about this, it just hurts :(1 -
I'd never do anything "risky" in a prod environment if I considered it so at the time, but in retrospect there's *lots* of things considered risky now (both from a security and good practice viewpoint) that were standard practice not long ago:
- Not using any form of version control
- No tests (including no unit tests)
- Not considering XSS vulnerabilities
- Completely ignoring CSRF vulnerabilities
- Storing passwords as unsalted MD5 hashes (heck that was considered very *secure* in the days of plaintext password storage.)
...etc. I'm guilty of all of those previously. I daresay in the future there will be yet more things that may be standard practice now, but become taboos we look back on with similar disdain.1 -
Social Captain (a service to increase a user's Instagram followers) has exposed thousands of Instagram account passwords. The company says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
According to TechCrunch : Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain text, as they had connected their account to the platform. A website bug allowed anyone access to any Social Captain user's profile without having to log in ; simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account and their Instagram login credentials. Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information easily. The security researcher who reported the vulnerability provided a spreadsheet of about 10,000 scraped user accounts to TechCrunch.3 -
Who's the dumbass that decided you can't delete your PayPal account at all unless your balance is $0?
I am not giving you my card information for the $0.18 balance I have. For God sakes, I don't even bend over to pick that up if I see it on the ground.
It's one thing if it were like $100 or even $10. But it's eighteen fucking cents. Not even a a quarter of a fucking dollar.
At least make me put in my password and answer a security question or some shit, not straight up remove the option to delete it.
Fucking ridiculous.21 -
Finally found my topic for the 10 min presentation :
Network protocol security
After giving an overview , i'm gonna talk about http , ftp , telnet , netbios and showing them a sample packet and how easy the username and password can be found if these protocols are used.
Any other recommandation?5 -
Security! I wish clients would listen to me regarding security...
The client has started to ask me to give them access to all the logins I have for the email, domain, server etc.
I created them a new account and gave them admin access.
Now they’re asking for password for all the email accounts (I don’t even store them). So I asked why, she wanted to have them in case some of the employees forgot their password.
I explained to her, deeply and many times, WHY THIS IS A BAD FUCKING IDEA. I also discovered she’s keeping it in a document, clear text.
Why do they pay me for support, when they want to have access to everything...
I’m wondering if they’re planning to find someone else to do their support, or do it themselves.
I didn’t even think 25€ pr month is that expensive for support2 -
Specifications called for user logins to be stored in a session and not be persistent. When the session ends, you need to login again. The system deals with insurance policy information and persistent login was deemed a security risk.
First ticket submitted by the client after go-live? "Please make the login page remember my user name and password, or that I've logged in previously."3 -
I am doing some freelance work for a client who is thankfully mindful about security. I found out that they are so strict with their access because they had a huge data breach last year.
Today I was given access to their repo for connecting to their AS400. In the docker file the username and password were included and were the same for dev and prod. They also are performing no sql injection prevention. They are just joining strings together.1 -
The most annoying hack I've had to deal with was back when I did IT support, actually. Level 1 call center tech at the time. Apparently someone fell for a phishing email and gave out his outlook credentials. The phisher used that email account to send out another phishing email to roughly 1800 employees.
Security Operations noticed, because this guy's job didn't generally involve sending out mass-communication emails. They investigated, figured out what had happened, and opted for the nuclear option: they reset the password for EVERY SINGLE ACCOUNT that received the email. All 1800 of them. Over the weekend.
I walked into the call center Monday morning and checked the call stats, then did a double-take. There were over 300 people waiting in the queue. I almost left and called in sick. Turns out it wasn't that bad though. Annoying to reset so many passwords and having no downtime due to the full queue, but on the other hand my stats were better that day than any other, since every call was a 5-minute password reset.1 -
Let's talk about the cargo cult of N-factor authentication. It's not some magic security dust you can just sprinkle onto your app "for security purposes".
I once had a client who had a client who I did server maintenance for. Every month I was scheduled to go to the site, stick my fingerprint in their scanner, which would then display my recorded face prominently on their screens, have my name and purpose verified by the contact person, and only then would the guards let me in.
HAHA no of course not. On top of all of that, they ask for a company ID and will not let me in without one.
Because after all, I can easily forge my face, fingerprints, on-site client contact, appointment, and approval. But printing out and laminating a company ID is impossible.
---
With apologies to my "first best friend" in High School, I've forgotten which of the dozens of canonicalisations of which of your nicknames I've put in as my answer to your security question. I've also forgotten if I actually listed you as my first best friend, or my dog - which would actually be more accurate - and actually which dog, as there are times in my High School life that there were more tails than humans in the house.
I have not forgotten these out of spite, but simply because I have also forgotten which of the dozen services of this prominent bullshit computer company I actually signed up for way back in college, which itself has been more than a decade ago. That I actually apparently already signed up for the service before actually eludes me, because in fact, I have no love for their myriad products.
What I have NOT forgotten is my "end of the universe"-grade password, or email, or full legal name and the ability to demonstrate a clear line of continuity of my identity from wherever that was to now.
Because of previous security screwups in the past, this prominent bullshit company has forced its users to activate its second, third, and Nth factors. A possibly decade-old security question; a phone number long lost; whatever - before you can use your account.
Note: not "view sensitive data" about the account, like full name, billing address, and contact info. Not "change settings" of the account, such as changing account info, email, etc. Apparently all those are the lowest tier of security meant to be protected by mere "end of the universe"-grade passwords and a second factor such as email, which itself is likely to be sold by a company that also cargo cults N-factor auth. For REAL hard info, let's ask the guy who we just showed the address to "What street he lived in" and a couple others.
Explaining this to the company's support hotline is an exercise in...
"It's for your security."
"It's not. You're just locking me out of my account. I can show you a government ID corroborating all the other account info."
"But we can't, for security."
"It's not security. Get me your boss."
...
"It's for security."8 -
Is it me or is password security is a giant mess right now?
Everyone has a gazillion ways to sign in.
Everything needs an account so eventually you get a password manager to keep track.
After reauthenticating passwordword manager, then you get to the next screen that requires you to enter a code from 2FA. Internet isn't fun to use any more.12 -
What the actual f. I just changed my password on uplay to a 30 character password which works fine on the web account manager. Apparantly some moron decided to limit password field in the uplay client where your actual games are stored to 17 or 18 characters.
And that while they want to "improve" security. Please ubisoft, fix your shit4 -
Hang on... If online banks ask you for the n'th, m'th and p'th character of your password, they must be storing it on plaintext! WTF? I don't even understand why they do that in the first place.11
-
Have you ever had the moment when you were left speechless because a software system was so fucked up and you just sat there and didn't know how to grasp it? I've seen some pretty bad code, products and services but yesterday I got to the next level.
A little background: I live in Europe and we have GDPR so we are required by law to protect our customer data. We need quite a bit to fulfill our services and it is stored in our ERP system which is developed by another company.
My job is to develop services that interact with that system and they provided me with a REST service to achieve that. Since I know how sensitive that data is, I took extra good care of how I processed the data, stored secrets and so on.
Yesterday, when I was developing a new feature, my first WTF moment happened: I was able to see the passwords of every user - in CLEAR TEXT!!
I sat there and was just shocked: We trust you with our most valuable data and you can't even hash our fuckn passwords?
But that was not the end: After I grabbed a coffee and digested what I just saw, I continued to think: OK, I'm logged in with my user and I have pretty massive rights to the system. Since I now knew all the passwords of my colleagues, I could just try it with a different account and see if that works out too.
I found a nice user "test" (guess the password), logged on to the service and tried the same query again. With the same result. You can guess how mad I was - I immediately changed my password to a pretty hard.
And it didn't even end there because obviously user "test" also had full write access to the system and was probably very happy when I made him admin before deleting him on his own credentials.
It never happened to me - I just sat there and didn't know if I should laugh or cry, I even had a small existential crisis because why the fuck do I put any effort in it when the people who are supposed to put a lot of effort in it don't give a shit?
It took them half a day to fix the security issues but now I have 0 trust in the company and the people working for it.
So why - if it only takes you half a day to do the job you are supposed (and requires by law) to do - would you just not do it? Because I was already mildly annoyed of your 2+ months delay at the initial setup (and had to break my own promises to my boss)?
By sharing this story, I want to encourage everyone to have a little thought on the consequences that bad software can have on your company, your customers and your fellow devs who have to use your services.
I'm not a security guy but I guess every developer should have a basic understanding of security, especially in a GDPR area.2 -
Fuck you Crapple.
I have to reset my password again just because I cant remember that one security question.
How the fuck am I supposed to know who my favourite primary school teacher is?11 -
*leaning back in the story chair*
One night, a long time ago, I was playing computer games with my closest friends through the night. We would meet for a whole weekend extended through some holiday to excessively celebrate our collaborative and competitive gaming skills. In other words we would definitely kick our asses all the time. Laughing at each other for every kill we made and game we won. Crying for every kill received and game lost. A great fun that was.
Sleep level through the first 48 hours was around 0 hours. After some fresh air I thought it would be a very good idea to sit down, taking the time to eventually change all my accounts passwords including the password safe master password. Of course I also had to generate a new key file. You can't be too serious about security these days.
One additional 48 hours, including 13 hours of sleep, some good rounds Call of Duty, Counter Strike and Crashday plus an insane Star Wars Marathon in between later...
I woke up. A tiereing but fun weekend was over again. After I got the usual cereals for breakfast I set down to work on one of my theory magic decks. I opened the browser, navigated to the Web page and opened my password manager. I type in the password as usual.
Error: incorrect password.
I retry about 20 times. Each time getting more and more terrified.
WTF? Did I change my password or what?...
Fuck.
Ffuck fuck fuck FUCKK.
I've reset and now forgotten my master password. I completely lost memory of that moment. I'm screwed.
---
Disclaimer: sure it's in my brain, but it's still data right?
I remembered the situation but until today I can't remember which password I set.
Fun fact. I also could not remember the contents of episode 6 by the time we started the movie although I'd seen the movie about 10 - 15 times up to that point. Just brain afk. -
***ILLEGAL***
so its IPL(cricket) season in india, there is a OTT service called hotstar (its like netflix of india), the cricket streams exclusively on hotstar..
so a quick google search reveals literally thousands of emails & passwords, found a pastebin containing 500 emails&passwords ...but those are leaked last year most of passwords are changed & many of them enabled 2FA.. after looking through them we can find some passwords are similar to their emails , some contains birth year like 1975,1997 etc, some passwords end with 123 ..so after trying a few different versions of the passwords like
1) password123 -> password@123, password1234
2) passwordyear -> password@year
2) for passwords similar to emails, we can add 123 ,1234, @ etc
created a quick python script for sending login requests
so after like 30-40 mins of work, i have 7 working accounts
*for those who have basic idea of security practices you can skip this part
lessons learnt
1) enable 2FA
2) use strong passwords, if you change your password , new password should be very different from the old one
there are several thousands of leaked plaintext passwords for services like netflix,spotify, hulu etc, are easily available using simple google search,
after looking through & analysing thousands of them you can find many common passwords , common patterns
they may not be as obvious as password ,password123 but they are easily guessable.
mainly this is because these type of entertainment services are used by the average joe, they dont care about strong passwords, 2FA etc6 -
So here I am investigating something our users are claiming. I look up which user the UserId did the change and I see not only the user but also the users password in clear text in a separate field. I thought that field was for a password hint that the user can set up, but I asked around and apparently, no... It's literally the plain text version of the password stored in the database, next to the hash of the password.
Apparently, the users were so impossible to deal with that we added that column and for users that constantly pester us about not knowing their password and not wanting to change it, we added a plaintext password field for them :D2 -
Security in defense is a joke.
New hire does not have accts set up told him over and over!
He decides to go into a classified area and just try. Common last name with first initial.
Guess what he was able to get in because no one changed the default password!
Yep now someone with an interim clearance got access to a machine that goes from unclass to secret and then top secret!6 -
When I see people using online tools to test the strength of their passwords I laugh at their stupidity 😭32
-
Microsoft Market:
"You tried a wrong password too many times"
(I know fucker, I made a fucking mistake because I had to restart the pc 20 fucking times already, I've got confused, you pc-fucker)
"The activity is temporarily suspended, try later"
LATER? WHEN? I need to work you moron. Just give me a number!!! 10 minutes? 10 hours? days?
Work on improving security, lazy sod, not on slowing my job.
PS As soon as I can I'll change the password in "ImpotentCrackWhoreFucker8==0-)"6 -
So for those of you keeping track, I've become a bit of a data munger of late, something that is both interesting and somewhat frustrating.
I work with a variety of enterprise data sources. Those of you who have done enterprise work will know what I mean. Forget lovely Web APIs with proper authentication and JSON fed by well-known open source libraries. No, I've got the output from an AS/400 to deal with (For the youngsters amongst you, AS/400 is a 1980s IBM mainframe-ish operating system that oriiganlly ran on 48-bit computers). I've got EDIFACT to deal with (for the youngsters amongst you: EDIFACT is the 1980s precursor to XML. It's all cryptic codes, + delimited fields and ' delimited lines) and I've got legacy databases to massage into newer formats, all for what is laughably called my "data warehouse".
But of course, the one system that actually gives me serious problems is the most modern one. It's web-based, on internal servers. It's got all the late-naughties buzzowrds in web development, such as AJAX and JQuery. And it now has a "Web Service" interface at the request of the bosses, that I have to use.
The programmers of this system have based it on that very well-known database: Intersystems Caché. This is an Object Database, and doesn't have an SQL driver by default, so I'm basically required to use this "Web Service".
Let's put aside the poor security. I basically pass a hard-coded human readable string as password in a password field in the GET parameters. This is a step up from no security, to be fair, though not much.
It's the fact that the thing lies. All the files it spits out start with that fateful string: '<?xml version="1.0" encoding="ISO-8859-1"?>' and it lies.
It's all UTF-8, which has made some of my parsers choke, when they're expecting latin-1.
But no, the real lie is the fact that IT IS NOT WELL-FORMED XML. Let alone Valid.
THERE IS NO ROOT ELEMENT!
So now, I have to waste my time writing a proxy for this "web service" that rewrites the XML encoding string on these files, and adds a root element, just so I can spit it at an XML parser. This means added infrastructure for my data munging, and more potential bugs introduced or points of failure.
Let's just say that the developers of this system don't really cope with people wanting to integrate with them. It's amazing that they manage to integrate with third parties at all...2 -
TLDR; Default admin login on WEP encrypted WLAN router for getting free stuff at my hair stylist studio.
Free WLAN in my hair stylist studio: They had their WEP key laying around in the waiting area. Well, I am not very happy with WEP, thought that they never heard of security. Found the default GW address, typed it into my browser and pressed Enter, logged in with admin/1234 and voila, I was root on their ADSL router 😌 Even more annoyed now from such stupidity I decided to tell the manager. All I told him was: You use a default login on your router, you give the WiFi password for free, WEP is very very insecure and can be hacked in seconds, and do you know what criminals will do with your internet access? He really was shocked about that last question, blank horror, got very pale in just one sec. I felt a little bit sorry for my harsh statement, but I think he got the point 😉 Next problem was: he had no clue how to do a proper configuration (he even didn't knew the used ISP username or such things). Telled me that 'his brother' has installed it, and that he will call him as soon as possible. Told him about everything he should reconfigure now, and saw him writing down the stuff on a little post-it.
Well, he then asked me what he can pay me? Told him that I don't want anything, because I would be happy when he changes the security settings and that is pay enough. He still insisted for giving me something, so I agreed on one of a very good and expensive hairwax. Didn't used it once 😁
Some weeks later when I was coming back for another hair cut: Free WLAN, logged in with admin/1234, got access and repeated all I did the last time once more 😎
HOW CAN YOU NOT LEARN FROM FAILS??2 -
What's a good password manager for Linux?
A few (optional) conditions (in order of preference):
1. It's free
2. It supports ssh, gpg, etc.
3. It has a GUI (a nice one with gtk/qt support)
4. It's (properly) secure
5. It has FIDO U2FA support (i.e. supports physical security keys like Yubikey or Solo)
6. It has a browser extension
7. It's compatible/non-conflicting with gnome-keyring16 -
If I have to change my domain password every 3 months for a bullshit out of date security policy (there's plenty of evidence suggesting that changing passwords is actually worse security), then maybe, just FUCKING maybe, make sure that that password change appropriately filters down to things like SQL Server so I can keep doing my goddamn work.9
-
ChaseBank is getting up my nose. Twice in four business days my account was flagged and I had to change my password for 'security' purposes. I spent the better part of 90 minutes in a futile attempt to find out why, when there's been no suspicious activity on my account, I'm being flagged. My father contacted a branch manager near him who told him to dial the priolrity customer service number and key in the letters (I shit you not) HO HO. I called the number. It's the same damn number I'd been calling. I called the branch. They told me I'd definitely receive a call back last Friday by 1800. No call. So, yesterday I called the manager of that branch, verified its location, told the manager he was supposed to call me by 1800 last Friday, and Chase Corporate would be in touch with him soon to explain that when you tell a customer you'll call them, you'll fucking call them.2
-
Rant rant rant!
Le me subscribe to website to buy something.
Le register, email arrives immediately.
*please not my password as clear text, please not my password as clear text *
Dear customer your password is: ***
You dense motherfucker, you special bread of idiotic asshole its frigging 2017 and you send your customer password in an email!???
They frigging even have a nice banner in their website stating that they protect their customer with 128bit cryptography (sigh)
Protect me from your brain the size of a dried pea.
Le me calm down, search for a way to delete his profile. Nope no way.
Search for another shop that sells the good, nope.
Try to change my info: nope you can only change your gender...
Get mad, modify the html and send a tampered form: it submits... And fail because of a calculation on my fiscal code.
I wanna die, raise as a zombie find the developers of that website kill them and then discard their heads because not even an hungry zombie would use that brains for something.1 -
Security is a joke. And people don't seem to get it. Especially Data mungers.
I've spent about half an hour trying to work out how to securely connect to power BI using PowerShell in a renewable manner for unattended access later on.
Every single example I've found seems to involve you storing $user and $password variables inside your script. If I'm lucky, they're going to pass them through ConvertTo-SecureString. And nobody talks about securely storing AD auth tokens, or using the Windows Credential Manager.
I know it's possible, but it's going to take me ages to work out how from all sorts of disparate sources...16 -
Ibwish I had remembered this when the weekly theme was office pranks.
In the first or second year of high school we covered basic internet security. Stuff like don't follow suspicious urls, don't open suspicious emails and such.
Our teacher let us play around with some sort of simulated desktop environment, where we could execute some hacks like ad popups and such on each other's environment, if we fell for the trap.
Anyways, one hack I found interesting was a hack, that lockes a user out of their virual desktop, until he enters a password, that will be displayed on his environment.
Yes, a very interesting hack, because it contains two obvious yet major design flaws, which I could exploit 😈
1. It's case sensitive
In itself not a problem, but combined with #2, it's fatal.
2. "IlIlllIlI"
Depending on your font, you probably have no idea what exactly I just typed.
Let's just say, the font displayed uppercase i and lowercase L completely undifferentiable.
Guess whom I let suffer.
It was our teacher, who had to demonstrate us some things and who was connected to the same network.
I swear, nothing beats that feeling when your tearcher has go come to you and embarrassingly ask you to "unhack" them, because they can't type it 😂1 -
So, i use this bulk messaging service and they decided to make logins OTP only ("for security reasons", they say), sent to your email.
So instead of entering a password quickly,
- enter the password for your email account,
- click about 10 times on Resend OTP
- wait for OTP
- copy OTP and paste in the box.
So basically relying on the person's email provider's security than deploying their own. -
tl;dr. web hosting && a panic attack && security threat
i wasn't sure whether my brother's domain was hosted or not (because it wasnt showing a website and he didnt know any better).
so i decided to host a react-app for it on netlify and pointed the domain's nameservers towards it (a separate security threat at bottom).
all went well and now when you punch in the domain it ..all-behold.. shows a website.
NOW, i remember my brother was using the domain's email which probably means it was hosted, right?. so im panicking because im not sure whether i just deleted all his emails or not because it's 1:15 am and he's asleep.
there is a rant in there somewhere but im in too much of a shock as to how much data i might have just accidentally deleted
.
.
another tl;dr: my domain registrar let me change someone else's settings..
the reason i didnt know his domain settings is that he didnt know his password.
i had bought a couple of domains and was gonna host them on netlify. while i was doing this a bright idea hit me.. "you should finally build a website for your brother for the domain he bought 7 years ago"..
this is where the fun begins.
i sent an email to my registrar to point all nameservers of all domains to my nameservers and just to try out i included my brother's domain into it (i dont own this domain it's not registered by my email), and the next day i get an email telling me they've successfully made all changes.
.
Now tomorrow is monday and i'm going to their office to tell them i found a security flaw and see how long i can stall before actually telling them what it was and how their live's could've been made hell.3 -
My journey into learning Docker, chapter {chapter++}:
Today I learned that when you use a database image in your docker-compose file, and you want to rebuild the whole thing for reasons (say, a big update), then if you change your credentials ("root" to "a_lambda_user" or change the db's password) for more security, and you rebuild and up the whole thing... It won't work. You'll get "access denied".
Because the database (at least mysql and mariadb) will persist somewhere, so you need to run "docker rm -v" even though you didn't use any volumes.
I love loosing my fucking time.4 -
Mooltipass.
It's an amazing Open Source project for a hardware based password manager. The community validates the security implementation and helps with improvements and streamlining.
My main go-to for password management now, made safer by Open Source.
https://github.com/limpkin/...1 -
Interesting password recommendation here...
Translation:
- A form with to fields: Surname and password.
- Below the form is a text: "For signup please enter your name and a password (e.g. your email address). With your name and password you can change your data anytime and may get access to the memberlist."
Bonus: There is a "help"-button (outside of the cutting) which even *recommends* the use of the email-address as the password!
Extra bonus: The password field is a normal text one.
IF THE EMAIL ADDRESS HAS TO BE SUBMITTED, WHY NOT JUST ADD ANOTHER FIELD OR AT LEAST LABEL THE FIELD CORRECTLY!
Update: After this form, you get to another form, to enter you email address... 3
3 -
When the login form tells me that my password is too short. The password that I've manually set in the database in my local dev environment.3
-
I think the fact that even Apple can't unlock your phone if you forget your passcode proves that they use very naive encryption method.
Suppose my data is "Hey This is Some Data" and Passcode is 1234, I could just Jumble this data using that passcode and It will be difficult to decrypt without Passcode. And If data is huge, it will be fairly impossible to do so. But that doesn't make it a good encryption method.
Such encryption, though safe is not practical, Imagine if there was no "Forget Password" Option on any account, I usually forgot my password very often when I was a child.
Apple has been doing such things for years, Using Bad things as a selling point. Apple users are dumb anyways because they don't want to control their phone.
Reset Password is a weak point which might be exploited but in such cases, usability is more important than security. Any service which doesn't allow resetting Password is a shitty service and I would never use such a service, They are too naive.689 -
I have to add an endpoint to integrate an API and I want to vomit when I think about this major security issue they introduce.
What type of prehistoric dumbass thought GET requests with username and password in the query parameters is a good idea to burden your partner with.4 -
I forgot my password to my mindfactory account, one of Germany's biggest online vendor for computer components. So I go through the resetting process, which is:
- apply for password reset
- get a mail
- confirm the mail
(So far, so good)
- get a mail with a new CLEAR TEXT PASSWORD
Is this the stone age!?
You never send an email containing the cleartext! You never even store the password as is!
You, as the provider, should never be able to know what the actual password was.
All you are supposed to do is to generate a random salt, and hash the user's password with the salt, and then you only store the salt and the hash. And whenever a user inputs their password, all you do is to check if the you can recreate the hash with the help of the salt and your hash algorithm. (There are libraries for that!)
If a user wants to reset their password? Send them to a mail with link on where they can assign a new password.
At no point should the password ever be stored or transmitted in any other medium.5 -
Nothing makes me not want to take a full-time job at your company more than having to go through IT tickets every quarter year when my password expires to actually change my password. Why have a fucking self-service portal for employees if logging in with an expired password doesn't work and the reset password link tells me that I need to log in to enroll with security questions (???). It feels like these websites are glued together with sticks and spit and there's a million of them each sporting one specific purpose! I have to go through this shit multiple times since I'm an intern and I didn't have access to my account through the course of the semester. Get your fucking shit together!1
-
Working at a local seo sweat-shop as "whatever the lead dev does't feel like doing" guy.
Inherit their linux "server".
- Over 500 security updates
- Everything in /var/www is chmod to 777
- Everything in /var/www is owned by a random user that isn't apache
- Every single database is owned by root sql user
- Password for sudo user and mysql root user same as wifi password given to everyone at company.
- Custom spaghetti code dashboard with over 400 files in one directory, db/ api logins spread throughout these files, passwords in plain text.
- Dashboard doesn't have passwords, just usernames to login
- Dashboard database has all customer information including credit card stored in plain text
- Company wifi is shared by other businesses in the area
I suggest that I should try to fix some of these things.
Lead Developer / Tech Director : We're an SEO company, not a security company . . .7 -
People, even on devrant, are complaining about having to change their Twitter passwords. A major security event is not the only occasion to change your password (for anything).
You should change your passwords for everything regularly. Like, once every month or two.
This is why password managers are brilliant.3 -
Have you ever thought to send a security code to the email the user put in the sign up form just to say him later "the password must contains at least 8 characters, etc." and ask him to fill the form again from scratch?
Who is so dumb to put the input check in this order? Honeywell.
- The email is correct?
- Ok, send a code and ask to confirm it
- The password meets the requirements?
- No, ask to confirm the email again just for fun.
I'll just ignore the waste of server resources to send N * Number of users emails for no reason.2 -
I just don't understand how people can be so careless with security. It's like every other fucking day you about 150 billion email address, SSNs, birth certificates, credit cards, private messages, you pet's medical records, and your personal DNA are fucking leaked and the best we got are "what street did you grow up on" to reset a password.2
-
Not only is the default password they set a piece of shit, the password field actually shows the password even after you save it, why even bother with security?
Hash your fucking passwords!
The internet kills my insides. 4
4 -
This kind of BS makes me mad
" - The password must have 6 digits
- It must have at most 2 repeated digits and 3 sequentials"
RIGHT, because 293417 is SO much safer than 999123
Btw, this is a phone company, so with this password you could probably have access to someone's phone number, phone records, address, and much more. WTF 1
1 -
I had to create an account on a website. I used LastPass to generate a strong password. I entered it and got the following message:
"Password must be between 8 and 16 characters and must have special characters (? , ! & #) and numbers"
My password was 20 characters, me annoyed to generate a 16 character password. Filled it in and got the same error. That was it for me.
Who dafuq limits a password to 16 characters, that's fucking nothing. It did not accept all special characters, only the ones that were showed (like 5 or so).
And here comes the worst part...
It's a bank website! I had to create the most most most insecure password in history for it to work.7 -
Back in https://devrant.com/rants/5492690 @Nihil75 referred to SlickVPN with a link, where you can buy a lifetime licence for $20. I thought - what the hell.. I don't need a public VPN rn, but for $20 for a lifetime lic - I'll take it, in case I'll ever need one.
I had some trouble signing up - the confirmation email never reached my inbox. So I got in touch with support. And they.... generated and send me a password in plain-text.
And there even isn't any nagging requirement to change the pass after I sign in for the first time!
IDK... As for a service claiming to be security-oriented, the first interaction already screams "INSECURE".
Well.. should still be OK for IP switching, to unlock Netflix content I guess. Don't need anything secure for that 🤷 15
15 -
At the beginning of the last year of university a new flatmate arrived. His father dropped him at the apartment and then called me asking for the Wi-Fi password.
I told him I could not remember it on the spot and I would tell it to his son later.
I actually remembered it very well and I could say I didn’t tell him because of security reasons …
Actually I was embarrassed to say on phone: “PubesRule!”
The password was actually decided by a previous flatmate…😅3 -
I know a doctor's practice which gives you your first name as a default password for your account. Watertight security for all these medical records :)
-
My country has the best security experts. They convince people that they are not thiefs, Then when people believe them and give them their data, They change the password.1
-
So just now I had to focus on a VM running in virt-manager.. common stuff, yeah. It uses a click of le mouse button to focus in, and Ctrl-Alt-L to release focus. Once focused, the VM is all there is. So focus, unfocus, important!
Except Mate also uses Ctrl-L to lock the screen. Now I actually don't know the password to my laptop. Autologin in lightdm and my management host can access both my account and the root account (while my other laptop uses fingerprint authentication to log in, but this one doesn't have it). Conveniently my laptop can also access the management host, provided a key from my password manager.. it makes more sense when you have a lot of laptops, servers and other such nuggets around. The workstations enter a centralized environment and have access to everything else on the network from there.
Point is, I don't know my password and currently this laptop is the only nugget that can actually get this password out of the password store.. but it was locked. You motherfucker for a lock screen! I ain't gonna restart lightdm, make it autologin again and lose all my work! No no no, we can do better. So I took my phone which can also access the management host, logged in as root on my laptop and just killed mate-screensaver instead. I knew that it was just an overlay after all, providing little "real" security. And I got back in!
Now this shows an important security problem. Lock screens obviously have it.. crash the lock screen somehow, you're in. Because behind that (quite literally) is your account, still logged in. Display managers have it too to some extent, since they run as root and can do autologin because root can switch user to anyone else on the system without authentication. You're not elevating privileges by logging in, you're actually dropping them. Just something to think about.. where are we just adding cosmetic layers and where are we actually solving security problems? But hey, at least it helped this time. Just kill the overlay and bingo bango, we're in!2 -
Hmmmm. Just looked at my security log for my outlook account. A bunch of unsuccessful sync attempts... from China, from South Africa, from Colombia, from Poland, from Vietnam, and from Brazil. All of them IMAP attempts. Good to know my password isn't compromised, but I think I'm going to reset it and double it's length, just to be sure.2
-
So a while back I had found a hole in a website's security, one that I has used pretty frequently. I was able to change my cookies and become any user I wanted. The only caveat was that I had to log in as a user in order to get things started. But once I was in I could basically be anyone I wanted to be just by changing a few numbers in the user ID of the cookie. They also did all of their user processing on the client side. Even password checks.
A couple weeks back I decided to go back in to see if anything had changed since then. It did! But not in the way I had thought.
So these guys decided that instead of fixing their security hole, they would have users just contact their people directly in order to get a new account.
Wow that's so much fucking overhead for basically being a lazy shit and not fixing the security holes. I mean how bad is your architecture if you can't go in and fix this?
Not only that I found that they actually stripped all of the users of their original subscriptions. So now if you want to get back on your subscription you'll have to fork over another $399. So that means going to their shitty form filling out your name, your number, email, and just hope that someone contacts you via phone call.
I'm glad I dropped this service. They clearly can't get their shit together.rant hackerman what the fuck are you doing bold and brash it's all shit more like belongs in the trash front end is shit back end is shit -
Im not sure if im a good or bad person by allowing my users to set a weak password.
They get to use almost whatever they want, but it may be bruteforced easily.
I let users decide their own security on that point.4 -
Signed up for an account on an online store, which then proceeded to send me my full password in plaintext, and in an unencrypted email.
Sent them an email 3 weeks ago detailing the security issue (i was extremely nice about it), but no response.
What else can i do?4 -
Challenge questions are so goddamn stupid.
Apparently I have an account with a certain online organization though I don't remember setting it up.
So naturally I had no idea of my username or password, so they asked me challenge questions.
It asked me the city of my birth, which is a place with a weird spelling. Because of that weird spelling, I never remember if I'm spelling it right (I was only there as a newborn infant) And I'm also supposed to remember if I capitalized it or not.
I hate challenge questions. And anyone doing any remotely simple research on me shouldn't have trouble learning what city I was born in so it seems to me it's a security vulnerability, nothing more.
And maybe I'm giving things away by saying it asks me that question, but it's a common security question any hacker would anticipate anyways.3 -
macs... I know I didn't like them before, but recently I wanted set up a vpn on another person's pc and first it didn't want to install because it was a third party program. understandable, change security settings, try again, works. and now... EVERY TIME the user wants to connect it asks for a password, because the vpn client is "changing system settings". whenever the pc is locked, it disconnects and asks for a password whenever you log in again.
The saying that macbooks "just work" has to be extended to "the most basic functionality kind of works, most of the time".
Or maybe I'm just ignorant and unable to handle the glory of mac osx4 -
Have any of you noticed how bad the new Google login page is? They invented reCAPTCHA, yet they use the old one. Considering how easy it is to make a mistake in the captcha and have to retype the password, people could start making shorter passwords (<16 characters) and seriously lower the security level of their accounts.4
-
Hi everyone,
One question is constantly popping in my head and I keep fighting to figure out how to answer.
So here it is:
Are you for or agains a password manager to store all your passwords?
P.S.
I am using a paid password manager, but keep asking myself is it really worth it, and am I compromising all my passwords if someone is willing to spend some time and hack my vaults. On the other hand the convenience and benefit of having all passwords in one place and also using different strong passwords for each of my accounts protects me from a weak security implementation on any third party service I use, because I am not re-using the same password everywhere.12 -
I recently went to an office to open up a demat account
Manager: so your login and password will be sent to you and then once you login you'll be prompted to change the password
Me: *that's a good idea except that you're sending me the password which could be intercepted* ok
Manager: you'll also be asked to set a security question...
Me: *good step*
Manager: ...which you'll need to answer every time you want to login
Me: *lol what? Maybe that's good but kinda seems unnecessary. Instead you guys could have added two factor authentication* cool
Manager: after every month you'll have to change your password
Me : *nice* that's good
Manager: so what you can do change the password to something and then change it back to what it was. Also to remember it keep it something on your number or some date
Me: what? But why? If you suggest users to change it back to what it was then what is the point of making them change the password in the first place?
Manager: it's so that you don't have to remember so many different passwords
Me: but you don't even need to remember passwords, you can just use softwares like Kaspersky key manager where you can generate a password and use it. Also it's a bad practice if you suggest people who come here to open an account with such methods.
Manager: nothing happens, I'm myself doing that since past several years.
Me: *what a fucking buffoon* no, sir. Trust me that way it gets much easier to get access to your system/account. Also you shouldn't keep your passwords written down like that (there were some password written down on their whiteboard)
Manager: ....ok...so yeah you need sign on these papers and you'll be done
Me:(looking at his face...) Umm..ok4 -
The most frustrating part of the "your password must be min. 8 characters long and include a number and a special character" thing is that it does not improve security.
On the contrary.
I wonder how many people in the company have the name of the city they are located in, and the current year in their password...
#newyork18 #beijing20173 -
For credential errors on login forms..
Do you guys follow the “OWASP standard” and won’t let the user know which field (email or password) was incorrect, just a general message or the more UX-way and let them know that it is for example the password that doesn’t match with given email (if it exists)? 🤔
Had a minor “discussion” about this with our sales-guy this afternoon why that I’m (as the full-stack, and only, developer there) not that of a fan about the UX-way.. (even thou ‘security’ is a “myth”). 😁9 -
Our customer's internal IT department isn't able to offer a solution for a single sign-on when the user needs to navigate into one of their apps. So they just show something like this before that happens: "For security reasons you'll have to enter your username and password again during the next step." Sure, that sounds believable. Oh boy.1
-
!rant
Many out there say you should use 2 factor authentication with everything, but personally i feel lile that would just turn your phone into a sigle point of failure.
Phisical security is my primary worry, because loosing your phone or having it stolen yould pretty much lock you out of all your accounts.
Another thing is i don't know as much about android security, and i wouldn't be confortable managing it.
I have 2FA active for some key services, but imho a strong password is usually enough. I think its far more more importat for your overall security to avoid passwords re-use.
What do you think? Do you have 2FA on all the time?9 -
I happened to purchase a multi currency card as I was preparing to travel abroad. I enquired a few non tech friends of mine about a bunch of providers/lenders and I got a consistent suggestion of how company XXX is safe and user friendly. I took a leap of faith and went with them, since I didn't have any time left to do my own research.
Met the vendor, loaded some money and all is well. At least so far.
I went to their website to create an account for checking my balance and to do a bunch of stuff online.
Nothing unusual so far.
I fill up the new user register page. At the end I get a message which says "SUCCESS" and asks me to check my email.
VOILA!
I have an email with my user id, password and security questions in CLEAR TEXT sitting in my inbox.
Good job XXX.1 -
When a junior develops an API call which return the user information and there is session_key and password encrypted in it too.
Dude! do you even know some basic security ! Please don't just Select * From table join table only !3 -
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
I fucking hate people who uses complex words to describe something simple.
Describing a frame work
Show-off : "..you can define what objects/tables to expose, what values in that object you want to expose...if you are using some orm, then because you have models defined. Once you update your model, your endpoints get the new model..."
Simpleton : "something like parse..."
Wtf is 'fixedUUID'?
Show-off: "..hardcoded UUID is fixed (constant) value, with format of UUID, hardcoded UUID will be unique value between backend and frontend,
you will need to store it as constant value in your codebase ( we may encrypt/ decrypt it for security reasons)..."
Simpleton : "a secret password only u & I know"
--why whyyyyyyyyyy2 -
One of our clients old CMS was completely hand written, allowed execution of PHP files in the uploads directory with an uploader that was publicly accessible, and the "security" was MD5 hashed passwords. Oh and the username/password for the admin user was password.
-
I know I'm a bit late with this, but I thought I'd share it anyway.
A few years ago me and my friend were messing around in computer class and I decided to look at the network devices.
I couldn't believe, what I saw. All of the school security cameras were there, and the best part: when I connected to their ip addresses, they were just showing the live feed, no password or anything.
I didn't really do anything with it since I couldn't think of any great ideas and it has since been fixed.
Technically not hacking but still somewhat related. -
Would it be clever to use a password manager with randomized passwords and also store them in chrome's password vault?
I mean it's less secure, yes, but should something bad really happen I can just change the password and this would be a good upgrade in terms of user experience
What do you guys think?16 -
We should find a way to replace passwords: any password manager which I tried is inaccurate in identifying login forms and is too hard to use for non technical people older than 40 and convince people to not use some stupid name + birth year combination as their passwords is a frustrating uphill battle.13
-
Lately, I've been working in a web security company (mainly as a Support guy).
Going through tickets, I've found one golden gem, which helped me realising how dum customers are.
Since he's our customer, we try to keep stuff up-and-running at all times. If something goes bad, we fix it, and we need their passwords for stuff.
After the customer (somehow) got hacked again, he changed the password in panic.
Note the initial password was really, really good.
He emailed us the new password for "just in case".
The password is "hard-to-guess".
What. The. Actuall. Fuck.
What's next?
Setting the password "12345", activating 2-step-authentication and sending his phone in, along with his finger so we can unlock it with touch id?2 -
rants[0] =
"tl;dr: the account creation process at salesforce.com is really flawed.
In a lecture we were supposed to try out different CRM tools, one of them was salesforce. They are the worlds largest CRM software provider - not relevant for the rant, but it means they should have enough $$$ and competence to make something better.
When you create your account, you do not set a password. Instead they send you an email with a link, serving both as account activation and for setting your password. However, if you close the tab without setting a password, your account is still activated and the link in the email won't work anymore.
Alright, rather annoying, but that's why you can reset your password via email, right? Wrong. When you try to reset your password, they prompt you with a security question. Even when you never set them up. And obviously can't give the right answer. Who designed this logic?
On top of that, they nicely tell you to contact your sys admin if you are still having issues. My account is private. Not associated with any company.
So yeah, burned 3 emails until I figured that out and created 3 accounts I can never access again."; -
I've been running Linux on my laptop natively for five months (since the 2nd week I got here). My boss and everyone on my team is okay with this. I've used Linux at the last three companies I've been at since 2012.
All I asked for was a Windows VM so I could use WebEx (which I did at my last job; used Win10 in Virtual box just to share my screen via x11vnc and reset my password occasionally). At my last job, they said Linux users were on their own, but they at least gave us a Windows ISO, license and ability to connect it to the domain. It was a west coast company, with 500 people in IT and several Linux users. The IT team at my current shop has known I've been running Linux for months.
Now the word has come down that I can't have Linux on my laptop and I need to put macos back on it (it's actually on there; just dual booting) for security or some shit. We have a massive deadline and project due in like two months and it would throw me off for several days if I needed to bring in and setup a personal laptop.
Fuck asking our worthless IT department for anything. I told the lead engineer I'd bring in my personal laptop before going back to Mac.2 -
My work network AD password has to be changed every 90 days or so and it is really getting to me now. I'm beginning to run out of passwords to use and may soon have to resort to writing them down on a piece of paper and lock it somewhere.
I get why we need to change it often. What I don't like is the stupid validation rules AD uses to check passwords. It doesn't allow variations and you have to use something completely new.
I have only been in the job for about 8 months and I have had a nightmare experience updating my password recently as the synchronisation failed and I was locked out of my accounts for a day or 2 rendering my useless and having to call support for help.
How the he'll am I supposed to remember my passwords when I have to change them that often!!!18 -
So I just got the cyber security pack on humblebundle... $15 for a year of PIA, a year of spider oak one cloud backups and a year of Dashlane are the notable ones (I’ll give away the antivirus ones for free since I don’t have windows).
But that wasn’t the awesomest part...
I installed Dashlane and after transferring all my stuff over from LastPass, I went to delete my LastPass
Dashlane autofilled the username...
It’s like so subtly aggressive in an unintentional way. Honestly this password manager Battle Royale is totally worth the $15 regardless.13 -
So, I’ve been given the task of sorting the security out in an application plugging the holes and whatnot as to be honest it’s shocking haha. It doesn’t help that we automate security audits but that’s a different rant for another day.
We’re using devise for authentication (rails standard, ♥️ devise), we have no password resets through the login page, it has to be manually reset by ringing support, why who knows, even though it’s built into the gem and we allow the user to login using an username instead of an email because for whatever reason someone thought it was a bright idea to not have the email field mandatory.
So I hop onto a call with the BAs, basically I go that we need to implement password resets into the login page so the user can do it themselves and also to cut down support calls a ticket is already in place for it. So I go through the standardised workflow for resetting a password. My manager goes.
“I don’t think this will be very secure”
Wait.. what. Have you never reset a password before? It’s following the same protocol as every other app.
We go back and fourth and I said I’ll get it checked with security just to keep him happy.
The issue mainly is well we can’t implement password resets due to 100s of users not having an email on there account.. 🙃 so before we push this change we need to try and notice all users to set a unique email.
Updated the tickets. All dandy.
Looking at the PRs to see what security things have been done if any and turns out one of the devs in India has just written a migration to add the same default email to every user that doesn’t have an email present and yep it got merged. So I go revert the change but talk about taking a “we don’t care about security approach”.
Eventually we want to have the user reset their passwords and login using their email and someone goes a head and does that. Not to mention the security risk.
Jesus Christ I wonder why I bother sometimes.2 -
Thats top notch design.
All actions happening on the page go to one endpoint. Removing old trusted computers, changing the password, changing 2FA, you name it.
Now if you want to remove all old trusted devices, you cannot remove all at once, there is no button for it. So you click one after the other. And then it stops working. Ok, then do the normal password rotation. Hmm, button has a loading spinner and then nothing happens.
Looking into the browser console:
- All requests go to /myaccount/security/graphql
- All requests get a 429 Too many requests
- Even if you just click a panel, it tracks the action to the graphql endpoint. Or at least tries to because even that gets shot down with a 429
Pretty dumb, eh? Must be some small shitty website. It's not. It's fucking paypal. -
You know what really grinds my gears? Products that have no right of linking your data to an online platform.
Case and point: Password Managers. Nearly all of them work only with an account on a given service, have the passwords stored on their servers and so on and so forth. There is 0 transparency and for that matter 0 security. I found my choice, though it infuriates me terribly.
Another thing are budget managers. The switch for YNAB from local to on servers really annoys me. They should have no business in storing my very private data on their server. I don't understand people using it either.1 -
Telegram or Signal? Got essentially blocked from Messenger because I was stupid enough to fold to peer pressure to get it for robotics and since I enabled it with a GV number they stopped allowing its use for specifically security checks while allowing it even to reset a password, and I somehow got a security check triggered, with no customer support and no ability to call with code, so I'm looking to switch. Even if I get Facebook back, I want to move to something at least that doesn't randomly trigger security checks and then has no customer support.rant messaging apps messenger fuck telegram mistake signal facebook no customer support why did i move all my chats there peer pressure i'm stupid12
-
Let's see:
No archival of data on a database server with over 5000 high profile customers using no encryption whatsoever with telnet open on LAN, every user on the same account in the office using the companies name as the password... But hey there are security cameras! -
Yeah, so when you create an account just about anywhere nowadays, you need to choose a strong password. Fair enough. But then, some sites/services/systems require a second password, sort of a password hint as an extra security for retrieving your first password in case you forget it. Well OK...That hint question just becomes very *in*secure when you must choose from some extremely stupid presets like "In which town were you born?" or "What was your mother's maiden name?", all of which are trivia that for most people can be easily googled, or looked up on facebook ffs. And these "in which town did this or that happen?" questions? As there is only one town in my country it's not a long shot that I was born in Mariehamn, met my partner in Mariehamn and had my first job in Mariehamn. Security questions for imbecils.4
-
I’m working on a new app I’m pretty excited about.
I’m taking a slightly novel (maybe 🥲) approach to an offline password manager. I’m not saying that online password managers are unreliable, I’m just saying the idea of giving a corporation all of my passwords gives me goosebumps.
Originally, I was going to make a simple “file encrypted via password” sort of thing just to get the job done. But I’ve decided to put some elbow grease into it, actually.
The elephant in the room is what happens if you forget your password? If you use the password as the encryption key, you’re boned. Nothing you can do except set up a brute-forcer and hope your CPU is stronger than your password was.
Not to mention, if you want to change your password, the entire data file will need to be re-encrypted. Not a bad thing in reality, but definitely kinda annoying.
So actually, I came up with a design that allows you to use security questions in addition to a password.
But as I was trying to come up with “good” security questions, I realized there is virtually no such thing. 99% of security question answers are one or two words long and come from data sets that have relatively small pools of answers. The name of your first crush? That’s easy, just try every common name in your country. Same thing with pet names. Ice cream flavors. Favorite fruits. Childhood cartoons. These all have data sets in the thousands at most. An old XP machine could run through all the permutations over lunch.
So instead I’ve come up with these ideas. In order from least good to most good:
1) [thinking to remove this] You can remove the question from the security question. It’s your responsibility to remember it and it displays only as “Question #1”. Maybe you can write it down or something.
2) there are 5 questions and you need to get 4 of them right. This does increase the possible permutations, but still does little against questions with simple answers. Plus, it could almost be easier to remember your password at this point.
All this made me think “why try to fix a broken system when you can improve a working system”
So instead,
3) I’ve branded my passwords as “passphrases” instead. This is because instead of a single, short, complex word, my program encourages entire sentences. Since the ability to brute force a password decreases exponentially as length increases, and it is easier to remember a phrase rather than a complicated amalgamation or letters number and symbols, a passphrase should be preferred. Sprinkling in the occasional symbol to prevent dictionary attacks will make them totally uncrackable.
In addition? You can have an unlimited number of passphrases. Forgot one? No biggie. Use your backup passphrases, then remind yourself what your original passphrase was after you log in.
All this accomplished on a system that runs entirely locally is, in my opinion, interesting. Probably it has been done before, and almost certainly it has been done better than what I will be able to make, but I’m happy I was able to think up a design I am proud of.8 -
Is it posible to change your devrant password? If yes where? Cause i cant find it (on phone or desktop)15
-
I have 2FA enabled on NPM so it would shut up about it, the recovery codes are in my password manager, right next to my secure randomly generated password.
Password authentication is fucking stupid.3 -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Let's play a game.
Theme: Security awareness - grey-hat style.
How to play:
Post the name of the site followed by actual bad-password restrictions of well-known companies in the comments.
If no-one beats me to it, I plan to share some of the more alarming ones(or all) on a twitter and tag the relative companies as well as various security enthusiasts.4 -
I’m in a tough spot - I’m completely overloaded with sysadmin type work (server upgrades, firewall and vendor coordination, security, password maintenance) that I don’t have time to complete any programming work assigned to me. My bosses are aware and have done their best to help, but I just can’t keep up (have two young kids too and just can’t work nights anymore without trouble at home). My bosses have been great, so I feel terrible about this, but I think I’m going to have to look for another employer, I can’t do this anymore. Am I a horrible person to leave them with so much work even though they tried to help me?8
-
During the cryptography & security lecture at the university I received an email from the university IT department with credentials to access the university cloud services. Of course, password was in a plain text.2
-
i once changed all of the passwords of my main online accounts(google, apple, facebook, telegram, outlook) as they weren't changed for years.
i decided unique and long passwords for each of them.😎
immediately after changing the passwords, i forgot all of them. 😵fortunately, i was able to reset.
Has this ever happened to anyone?3 -
Honestly my biggest rant in the past month hasn't been about code, It's about Windows 10 changing my desktop password to my Microsoft Account. I have certain security pet peeves and it just screams "telemetry"...
-
This tuesday I saw a really badly made PHP web application. Two actually. I was giving a time estimate for how long it would take to transfer these applications to our servers. While I was reading the code it became apparent that they had more security holes than Emmental cheese. Most views had obvious SQL-injection vulnerabilities and most probably XSS too. Although I didn't think too look for XSS in the moment. It just puzzled me that this bad code even exists.
But cherry on top was that the password wasn't checked at all. The login form was on the organization's website and was sent to the selected application. But the password wasn't checked in the application. And this was made by a real Finnish software development firm, like what the fuck.
Time to redo the applications I guess. Not like there's anything wrong in that if they pay for it.2 -
Do you guys remember a few days ago that I was looking for someone with certain email address because he didn't receive his email because HE had an insecure mail server? I was sad, because I love new members. While my site has everything public, even api urls to api services without any auth, email confirmation off, hardcoded links to internal servers like retoor42 in repositories, still someone managed to think he hacked me: https://retoor.molodetz.nl/hi/.... That guy! Ironically I went even looking for him to give him credentials! Listing all members of my site is even possible because I have literally right under in my site a link to the most advanced api ever where you can list everything the site contains THAT I ALLOW YOU TOO. That hacker says "magic". I have the url to that "magic" literally on every page Einstein.
Don't let that guy found out what you can do with api.molodetz.nl without any protection..
Dear lord. It's probably the most public site with no secrets ever.
Also, the server runs with a small password and it's a pwned password. Ssh is on port 22. No security measurements are taken.
I can assure you, I know security and worked on cloud shit for three years at one of Dutch biggest cloud provides, kinda aws.
You won't be able to do anything I don't want you to with causing big damage.
Dear lord.3 -
You just have to love it when a service at your company has the following character set to choose from [a-z][A-Z][0-9]. Not to bad, you might say... And then you realise that it needs to be 6-8 characters long. Who would design something like this?!? I'm happy that it's not too critical if something breaks.
-
Not super ranty but what I’m interested in how passwords are managed in your organisation?
I feel dirty receiving passwords through slack and having a spreadsheet on a shared drive seems like madness.
I’ve worked at organisations before that have a single login to a password manager. However theoretically I still have access to that as no one would have changed the password.
Organisational password manager softwares are really expensive!14 -
Company automatically disables your employee login passwords after every 45 days, which is a good practice for ensuring security. However I get no notifications that my password is being disabled. The result, for the past 4 months, I've been going to IT support requesting them to let me change my password on their admin console because I forgot to change it 'once again'. Sigh.. :/2
-
So I changed my FB account password and it gave me email notification with an ip address. And then when I logged in it gave me another notification email with a different IP address this time. Should I be concerned about my network security? This is just SO ANNOYING!!!2
-
I’m side-eyeing my apartment building’s management for emailing me a non-password-protected document that includes my Social Security number. 🤨4
-
Is OMEGA CRYPTO RECOVERY SPECIALIST a Genuine, Legit Lost Crypto Recovery Company.
OMEGA CRYPTO RECOVERY SPECIALIST is a company that was founded 22 years ago by a team of experts in the field of cryptocurrency. The company offers a range of services, including recovery of lost or inaccessible crypto assets, forensic analysis of blockchain transactions, and security consulting for individuals and businesses.
The company has gained a reputation in the industry for its expertise and professionalism, with many customers praising their services on social media and review sites. One of the key services offered by Omega Crypto Recovery Specialist is the recovery of lost or inaccessible crypto assets.
The company uses a variety of techniques and tools to recover lost assets, including forensic analysis of blockchain transactions, brute-force password cracking, and social engineering. The company also offers security consulting services for individuals and businesses to help prevent future losses.
Webpage: omegarecoveryspecialist . c o m4 -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
Is it possible to add a layer of security such as a password when you use Thunderbird Mail application? So when you open it, it would require a password to proceed checking mails etc..6
-
I can't recall what platform it was, but upon trying to change my password it would tell me that the new password was too similar to the previous one... :/1
-
Someone earlier today posted a rant about a credit card security conference sending them account details with a plain text password in an email. The password appeared to be 1 use temporary password that the user would change on first login. Assuming one does not actually store plain text passwords, what is the downside to a single use password Vs a single use link to set a new password?1
-
Whenever a site tells me the password I entered has already been used? I mean how are you supposed to know if you are salting and hashing the password.. Oh wait you probably just save it in plain text!! Please don't!!7
-
What's harder than trying to name a variable is to think of a memorable but easy to type password to a system that resets expires every 3 months with history checks.2
-
Can anyone recommend a good password manager that is 'in the cloud', can be used on my mobile and makes life easy for logging into apps on my phone that aren't logged in via a browser. Ideally something free but I'm willing to pay for something that is worth it8
-
Who Is The Best Hacker To Recover Stolen || Scammed Bitcoin || Hire ULTIMATE HACKER JERRY
In the event of crypto theft or loss, quick action is essential. ULTIMATE HACKER JERRY provides people in need with timely and attentive support. Their staff is prepared to start the recovery process as soon as possible because they recognize how urgent the situation is.Apart from recovery, ULTIMATE HACKER JERRY equips customers with information on preventive security measures. In order to avert such incidents, clients are given advice on how to improve their overall security posture, apply best practices for password management, and make use of extra security layers. 22
22